Konica Minolta bizhub 36 bizhub 36/42 Administrator Operations User Guide - Page 149
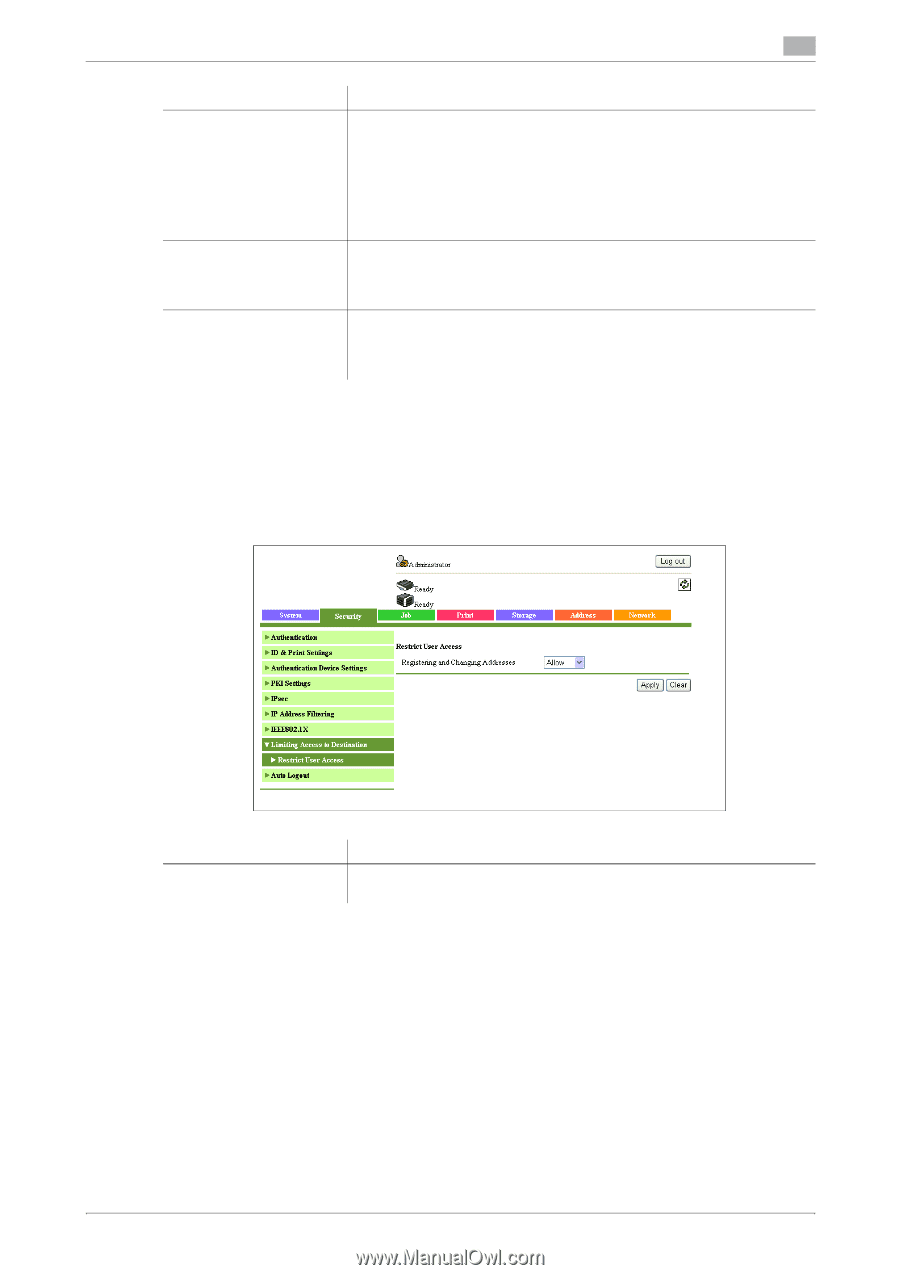
Limiting Access to Destination], Restrict User Access]
 |
View all Konica Minolta bizhub 36 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 149 highlights
5.2 [Security] tab Item [Encryption Strength] [Network Stop] [Limit Time] 5 Description Select an encryption strength level for encrypted communication with TLS. • [Low]: Keys of any length are used for communication. • [Medium]: Keys that are more than 56 bits in length are used for com- munication. • [High]: Keys that are more than 128 bits in length are used for commu- nication. This item is available if [EAP-Type] is set to anything other than [None] or [EAP-MD5]. If an authentication process does not succeed within the specified time, all network communication will stop. To specify the delay between the start of an authentication process and the stop of network communication, select [Enable]. Specify the delay (sec.) between the start of an authentication process and the stop of network communication. To restart the authentication process after network communication has stopped, turn the power of this machine off and on again. 5.2.8 [Limiting Access to Destination] You can configure the setting that prohibits user operation. [Restrict User Access] Select [Security] ö [Limiting Access to Destination] ö [Restrict User Access]. Item [Registering and Changing Addresses] Description Select whether or not to prohibit users from registering or editing destinations. bizhub 42/36 5-61