HP 8/8 Fabric OS Encryption Administrator's Guide v6.4.0 (53-1001864-01, June - Page 180
Deployment with FCIP extension switches
 |
View all HP 8/8 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 180 highlights
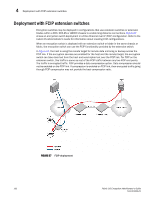
4 Deployment with FCIP extension switches Deployment with FCIP extension switches Encryption switches may be deployed in configurations that use extension switches or extension blades within a DCX, DCX-4S or 48000 chassis to enable long distance connections. Figure 67 shows an encryption switch deployment in a Fibre Channel over IP (FCIP) configuration. Refer to the Fabric OS Administrator's Guide for information about creating FCIP configurations. When an encryption switch is deployed with an extension switch or blade in the same chassis or fabric, the encryption switch can use the FCIP functionality provided by the extension switch. In Figure 67, the host is using the remote target for remote data mirroring or backup across the FCIP link. If the encryption services are enabled for the host and the remote target, the encryption switch can take clear text from the host and send cipher text over the FCIP link. For FCIP on the extension switch, this traffic is same as rest of the FCIP traffic between any two FCIP end points. The traffic is encrypted traffic. FCIP provides a data compression option. Data compression should not be enabled on the FCIP link. If compression is enabled on FCIP link, then encrypted traffic going through FCIP compression may not provide the best compression ratio. FIGURE 67 FCIP deployment 162 Fabric OS Encryption Administrator's Guide 53-1001864-01