HP 8/8 Fabric OS Encryption Administrator's Guide v6.4.0 (53-1001864-01, June - Page 184
Firmware download considerations, Firmware Upgrades and Downgrades
 |
View all HP 8/8 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 184 highlights
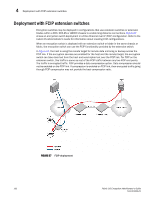
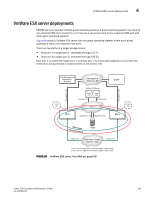
5 Firmware download considerations Firmware download considerations The encryption engine and the control processor or blade processor are reset after a firmware upgrade. Disruption of encryption I/O can be avoided if an HA cluster is configured. If encryption engines are configured in an HA cluster, perform firmware upgrades one encryption engine at a time so that the partner switch in the HA cluster can take over I/O by failover during firmware upgrade. When switches form a DEK cluster, firmware upgrades should also be performed one at a time for all switches in the DEK cluster to ensure that a host MPIO failover path is always available. Firmware Upgrades and Downgrades You cannot downgrade to a Fabric OS version release prior to Fabric OS version 6.2.0. A downgrade to Fabric OS version 6.2.0 results in the loss of the following functionality. • If an TEMS key vault is being used, a downgrade to v6.2.0 results in a loss of encryption services. • Fabric OS version 6.2.0 supports only one HP SKM key vault. Registering of a second HP SKM key vault will be blocked. • Fabric OS version 6.2.0 uses brcduser1 as a standard user name when creating a Brocade group on SKM. If you downgrade from version 6.3.0 or later to version 6.2.0, the user name is overwritten to brcduser1, and the Brocade group user name must be changed to brcduser1. • General guidelines for a firmware upgrade of encryption switches and a DCX or DCX-4S with encryption blades in encryption groups, HA clusters, and DEK clusters are as follows: - Upgrade one node at time. - Do not do a firmware upgrade when re-key operations and first time encryption operations are underway. - Do not start any manual re-key operations and first time encryption operations during the firmware upgrade process for all nodes in the HA/DEK cluster. • Guidelines for firmware upgrade of encryption switches and a DCX or DCX-4S with encryption blades deployed in a DEK cluster with two HA clusters: - Upgrade nodes in one HA cluster at a time. - Within an HA cluster, upgrade one node at a time. • Guidelines for firmware upgrade of encryption switches and a DCX or DCX-4S with encryption blades deployed in DEK cluster with No HA cluster (each node hosting one path. - Upgrade one node at a time. - In the case of active/passive arrays, upgrade the node which is hosting the passive path first. Upgrade the node which is hosting active path next. The Host MPIO ensures that I/O fails over and fails back from active to passive and back to active during this firmware upgrade process. - In the case of active/active arrays, upgrade order of nodes does not matter, but you still must upgrade one node at a time. The Host MPIO ensures that I/O fails over and fails back from one active path to another active path during this firmware upgrade process. • All nodes in an encryption group must be at the same firmware level before starting a re-key or first time encryption operation. 166 Fabric OS Encryption Administrator's Guide 53-1001864-01