D-Link DES-3550 Product Manual - Page 217
CPU Filtering Settings, ARP Spoofing Prevention, Apply, Filtering Status - L3 Control Packet, Security
 |
UPC - 790069266317
View all D-Link DES-3550 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 217 highlights
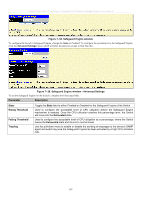
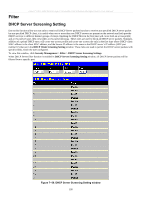
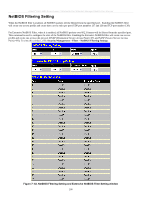
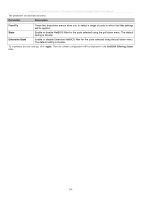
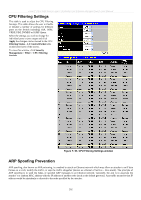
xStack® DES-3500 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual CPU Filtering Settings This table is used to adjust the CPU Filtering Settings. This table allows the user to Enable or Disable a number of settings for different ports on the Switch including; RIP, OSPF, VRRP, PIM, DVMRP or IGMP Query. Select the settings you wish to change for individual ports or port ranges and click Apply the changes can be viewed in the CPU Filtering Status - L3 Control Packet table on the lower have of the screen. To view this window, click Security Management > Filter > CPU Filtering Settings. Figure 7- 63. CPU Filtering Settings window ARP Spoofing Prevention ARP spoofing, also known as ARP poisoning, is a method to attack an Ethernet network which may allow an attacker to sniff data frames on a LAN, modify the traffic, or stop the traffic altogether (known as a Denial of Service - Dos attack). The principle of ARP spoofing is to send the fakes, or spoofed ARP messages to an Ethernet network. Generally, the aim is to associate the attacker's or random MAC address with the IP address of another node (such as the default gateway). Any traffic meant for that IP address would be mistakenly re-directed to the node specified by the attacker. 202