Netgear WGR614v10 Reference Manual - Page 33
Open System, Shared Key, Passphrase, Wireless Settings, Apply, Wireless-G Router - access point setup
 |
View all Netgear WGR614v10 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 33 highlights
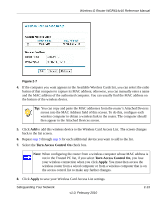
Wireless-G Router WGR614v10 Reference Manual WEP offers the following options: • Open System. With Open System authentication and 64 or 128 bit WEP data encryption, the Wireless-G Router does perform data encryption but does not perform any authentication. Anyone can join the network. This setting provides very little practical wireless security. • Shared Key. With Shared Key authentication, a wireless device must know the WEP key to join the network. Select the encryption strength (64 or 128 bit data encryption). Manually enter the key values, or enter a word or group of printable characters in the Passphrase field. Manually entered keys are not case-sensitive, but passphrase characters are case-sensitive. To configure WEP data encryption: Note: If you use a wireless computer to configure WEP settings, you will be disconnected when you click Apply. You must then either configure your wireless adapter to match the wireless router WEP settings or access the wireless router from a wired computer to make any further changes. Not all wireless adapter configuration utilities support passphrase key generation. 1. Select Wireless Settings under Setup in the main menu. 2. In the Security Options section, select WEP. The WEP options display. . Figure 2-3 3. Select the authentication type and encryption strength. 4. You can manually or automatically program the four data encryption keys. These values must be identical on all computers and access points in your network. Safeguarding Your Network 2-8 v1.0, February 2010