Linksys WAG54G User Guide - Page 73
Step 3: Con Individual Tunnel Rules, Tunnel 1: win->Gateway
 |
View all Linksys WAG54G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 73 highlights
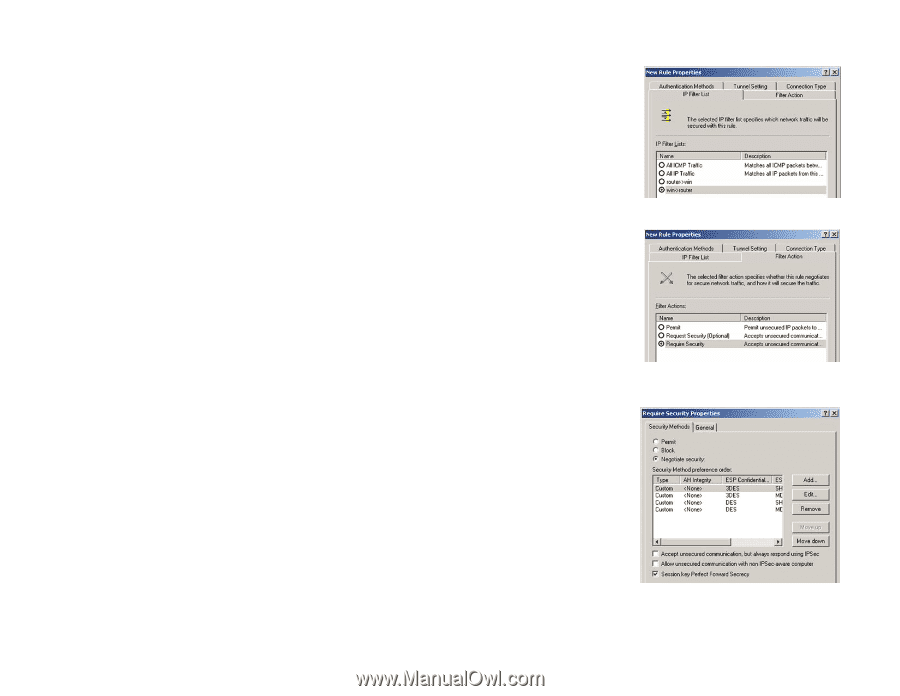
Wireless-G ADSL Gateway Step 3: Configure Individual Tunnel Rules Tunnel 1: win->Gateway 1. From the IP Filter List tab, shown in Figure C-10, click the filter list win->Gateway. 2. Click the Filter Action tab (as in Figure C-11), and click the filter action Require Security radio button. Then, click the Edit button. 3. From the Security Methods tab, shown in Figure C-12, verify that the Negotiate security option is enabled, and deselect the Accept unsecured communication, but always respond using IPSec check box. Select Session key Perfect Forward Secrecy, and click the OK button. Figure C-10: IP Filter List Tab Figure C-11: Filter Action Tab Appendix C: Configuring IPSec between a Windows 2000 or XP Computer and the Gateway How to Establish a Secure IPSec Tunnel Figure C-12: Security Methods Tab 66