ZyXEL VSG1432-B101 User Guide - Page 252
Table 87
 |
View all ZyXEL VSG1432-B101 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 252 highlights
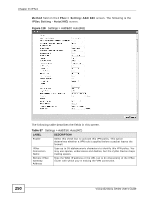
Chapter 21 IPSec Table 87 Settings > Add/Edit: Auto(IKE) LABEL DESCRIPTION Authentication Method Select Pre-Shared Key to use a pre-shared key for authentication. A pre-shared key identifies a communicating party during a phase 1 IKE negotiation. It is called "pre-shared" because you have to share it with another party before you can communicate with them over a secure connection. Pre-Shared Key Select Certificates (X.509) to use a certificate for authentication. This field is available only when you select Pre-Shared Key in the Authentication Method field. Type up to 15 alphanumeric characters for the pre-shared key. Both ends of the VPN tunnel must use the same pre-shared key. You will receive a "PYLD_MALFORMED" (payload malformed) packet if the same pre-shared key is not used on both ends. Local/Remote ID Select IP to identify this ZyXEL Device by its IP address. Type Select DNS to identify this ZyXEL Device by a domain name. Select E-mail to identify this ZyXEL Device by an e-mail address. Select ASN1DN (Abstract Syntax Notation one - Distinguished Name) to identify the remote IPSec router by the subject field in a certificate. This is used only with certificate-based authentication. Local/Remote ID When you select IP in the Local/Remote ID Type field, type the IP Content address of your computer in the Local/Remote ID Content field. When you select DNS or E-mail in the Local/Remote ID Type field, type a domain name or e-mail address by which to identify this ZyXEL Device in the Local/Remote ID Content field. Use up to 31 ASCII characters including spaces, although trailing spaces are truncated. The domain name or e-mail address is for identification purposes only and can be any string. Advanced IKE Settings Click Show Advanced Settings to display and configure more detailed settings of your IKE key management. Otherwise, click Hide Advanced Settings. NAT_Traversal Select Enable if you want to set up a VPN tunnel when there are NAT routers between the ZyXEL Device and remote IPSec router. The remote IPSec router must also enable NAT traversal, and the NAT routers have to forward UDP port 500 packets to the remote IPSec router behind the NAT router. Otherwise, select Disable. Phase 1/Phase 2 Mode Select Main or Aggressive from the drop-down list box. Multiple SAs connecting through a secure gateway must have the same negotiation mode. 252 VSG1432-B101 Series User's Guide