D-Link DGS-3048 Product Manual - Page 107
SSH Configuration, SSH Algorithm, Current SSH Configuration Settings Window, Parameter
 |
UPC - 790069287367
View all D-Link DGS-3048 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 107 highlights
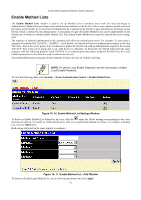
DGS-3048 Gigabit Ethernet Switch Manual The steps required to use the SSH protocol for secure communication between a remote PC (the SSH client) and the Switch (the SSH server) are as follows: 1. Create a user account with admin-level access using the User Accounts window in the Administration folder. This is identical to creating any other admin-level User Account on the Switch, including specifying a password. This password is used to logon to the Switch, once a secure communication path has been established using the SSH protocol. 2. Configure the User Account to use a specified authorization method to identify users that are allowed to establish SSH connections with the Switch using the Current Accounts window (Security > Secure Shell (SSH) > SSH User Authentication). There are three choices for the method SSH will use to authorize the user: HostBased, Password, and Public Key. Otherwise choose the the fourth option, None. 3. Configure the encryption algorithm that SSH will use to encrypt and decrypt messages sent between the SSH client and the SSH server, using the Encryption Algorithm window. 4. Finally, enable SSH on the Switch using the SSH Configuration window. After completing the preceding steps, a SSH Client on a remote PC can be configured to manage the Switch using a secure, in band connection. SSH Configuration The following window is used to configure and view settings for the SSH server and can be opened by clicking Security > Secure Shell (SSH) > SSH Configuration: Figure 10- 20. Current SSH Configuration Settings Window To configure the SSH server on the Switch, modify the following parameters and click Apply: Parameter Description SSH Server Status Port (1-65535) Use the pull-down menu to enable or disable SSH on the Switch. The default is Disabled. The TCP port number currently being utilized by the Switch to connect to the SSH server. The "well-known" TCP port for SSH management is 22. SSH Algorithm This window allows the configuration of the desired types of SSH algorithms used for authentication encryption. There are three categories of algorithms listed and specific algorithms of each may be enabled or disabled by using their corresponding pull-down menus. All algorithms are enabled by default. To open the following window, click Security > Secure Shell (SSH) > SSH Algorithm: 95