D-Link DGS-3048 Product Manual - Page 90
Security, Port Access Entity, 1x Port-Based Access Control
 |
UPC - 790069287367
View all D-Link DGS-3048 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 90 highlights
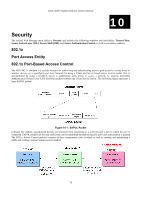
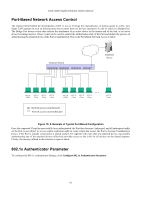
DGS-3048 Gigabit Ethernet Switch Manual 10 Security The second Web Manager main folder is Security and includes the following windows and sub-folders: Trusted Host, Secure Socket Layer (SSL), Secure Shell (SSH), and Access Authentication Control, as well as secondary windows. 802.1x Port Access Entity 802.1x Port-Based Access Control The IEEE 802.1x standard is a security measure for authorizing and authenticating users to gain access to various wired or wireless devices on a specified Local Area Network by using a Client and Server based access control model. This is accomplished by using a RADIUS server to authenticate users trying to access a network by relaying Extensible Authentication Protocol over LAN (EAPOL) packets between the Client and the Server. The following figure represents a basic EAPOL packet: Figure 10- 1. EAPOL Packet Utilizing this method, unauthorized devices are restricted from connecting to a LAN through a port to which the user is connected. EAPOL packets are the only traffic that can be transmitted through the specific port until authorization is granted. The 802.1x Access Control protocol consists of three components, each of which is vital to creating and maintaining a stable and working Access Control security method. 78