D-Link DI-707P Product Manual - Page 8
Introduction to Virtual Private Networking, Point-to-Point Tunneling Protocol PPTP, IP Security - vpn
 |
UPC - 790069241000
View all D-Link DI-707P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 8 highlights
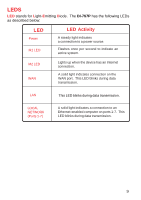
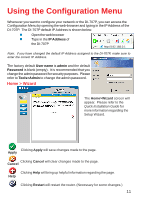
Introduction to Virtual Private Networking Virtual Private Networking (VPN) uses a publicly wired network (the Internet) to securely connect two different networks as if they were the same network. For example, an employee can access the corporate network from home using VPN, allowing the employee to access files and printers. Here are several different implementations of VPN that can be used. Point-to-Point Tunneling Protocol (PPTP) PPTP uses proprietary means of connecting two private networks over the Internet. PPTP is a way of securing the information that is communicated between networks. PPTP secures information by encrypting the data inside of a packet. IP Security (IPSec) IPSec provides a more secure network-to-network connection across the Internet or a Wide Area Network (WAN). IPSec encrypts all communication between the client and the server whereas PPTP only encrypts the data packets. Both of these VPN implementations are used because there is not a standard for VPN server software. Because of this, each ISP or business can implement its own VPN network making interoperability a challenge. 8