Lexmark T652DTN Embedded Web Server Administrator's Guide - Page 25
Configuring security audit log settings, E-mail server setup
 |
UPC - 734646317368
View all Lexmark T652DTN manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 25 highlights
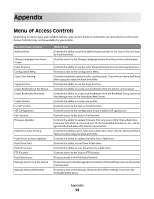
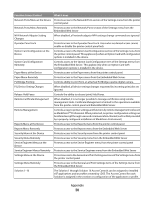
The printer will power-on reset, and then return to normal operating mode. Configuring security audit log settings The security audit log allows administrators to monitor security-related events on a device including, among others, user authorization failures, successful administrator authentication, or Kerberos files being uploaded to a device. By default, security logs are stored on the device, but may also be transmitted to a network syslog server for further processing or storage. 1 From the Embedded Web Server Home screen, select Settings ª Security ª Security Audit Log. 2 Select Enable Audit to activate security audit logging (syslog). 3 To transmit log events to a network syslog server, type the IP address or hostname of the Remote Syslog Server, and then select the Enable Remote Syslog check box. Note: The Enable Remote Syslog check box will be grayed out until an IP address or hostname is entered. 4 Type the Remote Syslog Port number used on the destination server. The default value is port 514. 5 From the Remote Syslog Method list, select Normal UDP (to send log messages and events using a lower-priority transmission protocol) or Stunnel (if implemented on the destination server). 6 From the Remote Syslog Facility list, select a facility code for events to be logged to on the destination server. All events sent from the device will be tagged with the same facility code to aid in sorting and filtering by network monitoring or intrusion detection software. Note: Steps 4 through 6 are valid only if Remote Syslog is enabled. 7 From the Severity of events to log list, select the priority level cutoff (0-7) for logging messages and events. 0 is the highest severity, and 7 is the lowest. The chosen severity level and anything higher will be logged (e.g. if level "4 - Warning" is chosen, severity levels 0-4 will be logged). 8 To send all events regardless of severity to the remote server, select the Remote Syslog non-logged events check box. 9 To have administrators automatically notified of certain log events, type one or more E-mail addresses (separated by commas) in the Admin's e-mail address field, and then choose from the following options: E-mail log cleared alert-When the Delete Log button is clicked E-mail log wrapped alert-When the log becomes full and begins to overwrite the oldest entries Log full behavior-Wrap over oldest entries, or E-mail log then delete E-mail % full alert-When log storage space reaches a certain percentage of capacity % full alert level (1-99%)-How full the log must be before an alert is triggered E-mail log exported alert-When the log file is exported E-mail log settings changed alert-When log settings are changed Note: In order to use E-mail alerts, you must click Submit to save changes, and then follow the Setup E-mail Server link to configure SMTP settings. 10 Click Submit to save changes, or Reset Form to restore default values. E-mail server setup 1 From the Security Audit Log main screen, select Setup E-mail Server. 2 Under SMTP Setup, type the IP address or hostname of the Primary SMTP Gateway the device will use for sending E-mail. Using security features in the Embedded Web Server 25