ZyXEL LTE5121 User Guide - Page 125
Firewall
 |
View all ZyXEL LTE5121 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 125 highlights
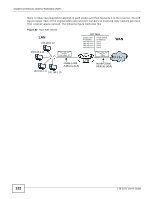
CHAPTER 12 Firewall 12.1 Overview Use the LTE Device firewall screens to enable and configure the firewall that protects your LTE Device and network from attacks by hackers on the Internet and control access to it. By default the firewall: • Allows traffic that originates from your LAN computers to go to all other networks. • Blocks traffic that originates on other networks from going to the LAN. The following figure illustrates the default firewall action. User A can initiate an IM (Instant Messaging) session from the LAN to the WAN (1). Return traffic for this session is also allowed (2). However other traffic initiated from the WAN is blocked (3 and 4). Figure 84 Default Firewall Action LAN 1 A 2 WAN 3 4 12.1.1 What You Can Do in this Chapter • Use the General screen to enable or disable the LTE Device's firewall and set the security level (Section 12.2 on page 126). • Use the Services screen to view the configured firewall rules and add, edit or remove a firewall rule (Section 12.3 on page 127). • Use the Access Control screen to view and configure incoming/outgoing filtering rules (Section 12.4 on page 129). • Use the DoS screen to enable or disable Denial of Service (DoS) protection (Section 12.5 on page 131). LTE-5121 User's Guide 125