ZyXEL NWA1123-NI User Guide - Page 90
Security Mode Guideline
 |
View all ZyXEL NWA1123-NI manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 90 highlights
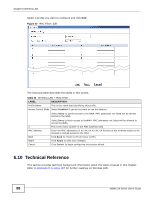
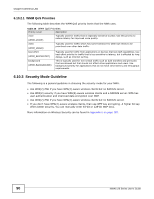
Chapter 6 Wireless LAN 6.10.2.1 WMM QoS Priorities The following table describes the WMM QoS priority levels that the NWA uses. Table 25 WMM QoS Priorities Priority Level description voice (WMM_VOICE) Typically used for traffic that is especially sensitive to jitter. Use this priority to reduce latency for improved voice quality. video (WMM_VIDEO) Typically used for traffic which has some tolerance for jitter but needs to be prioritized over other data traffic. best effort (WMM_BESTEFFORT) Typically used for traffic from applications or devices that lack QoS capabilities. Use best effort priority for traffic that is less sensitive to latency, but is affected by long delays, such as Internet surfing. background (WMM_BACKGROUND) This is typically used for non-critical traffic such as bulk transfers and print jobs that are allowed but that should not affect other applications and users. Use background priority for applications that do not have strict latency and throughput requirements. 6.10.3 Security Mode Guideline The following is a general guideline in choosing the security mode for your NWA. • Use WPA(2)-PSK if you have WPA(2)-aware wireless clients but no RADIUS server. • Use WPA(2) security if you have WPA(2)-aware wireless clients and a RADIUS server. WPA has user authentication and improved data encryption over WEP. • Use WPA(2)-PSK if you have WPA(2)-aware wireless clients but no RADIUS server. • If you don't have WPA(2)-aware wireless clients, then use WEP key encrypting. A higher bit key offers better security. You can manually enter 64-bit or 128-bit WEP keys. More information on Wireless Security can be found in Appendix E on page 187. 90 NWA1120 Series User's Guide