D-Link DFL-200 Product Manual - Page 70
How to read the logs, USAGE events, DROP events - open ports
 |
UPC - 790069268823
View all D-Link DFL-200 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 70 highlights
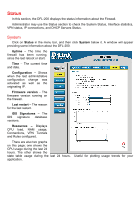
How to read the logs Although the exact format of each log entry depends on how your SYSLog recipient works, most are very similar. The way in which logs are read is also dependent on how your SYSLog recipient works. SYSLog daemons on UNIX servers usually log to text files, line by line. Most SYSLog recipients preface each log entry with a timestamp and the IP address of the machine that sent the log data: Oct 20 2003 09:45:23 gateway This is followed by the text the sender has chosen to send. All log entries from the DFL200 are prefaced with "EFW:" and a category, e.g. "DROP:" Oct 20 2003 09:45:23 gateway EFW: DROP: Subsequent text is dependent on the event that has occurred. USAGE events These events are sent periodically and provide statistical information regarding connections and amount of traffic. Example: Oct 20 2003 09:45:23 gateway EFW: USAGE: conns=1174 if0=core ip0=127.0.0.1 tp0=0.00 if1=wan ip1=192.168.10.2 tp1=11.93 if2=lan ip2=192.168.0.1 tp2=13.27 if3=dmz ip3=192.168.1.1 tp3=0.99 The value after "conns" is the number of open connections through the firewall when the usage log was sent. The value after "tp" is the throughput through the firewall at the time the usage log was logged. DROP events These events may be generated by a number of different functions in the firewall. The most common source is the policies. Example: Oct 20 2003 09:42:25 gateway EFW: DROP: prio=1 rule=Rule_1 action=drop recvif=wan srcip=192.168.10.2 destip=192.168.0.1 ipproto=TCP ipdatalen=28 srcport=3572 destport=135 tcphdrlen=28 syn=1 In this line, traffic from 192.168.10.2 coming from the WAN side of the firewall, connecting to 192.168.10.1 on port 135 is dropped. The protocol used is TCP. 70