Linksys SPA921 Cisco Small Business IP Telephony Devices Provisioning Guide - Page 21
Using HTTPS, Provisioning Cisco Small Business VoIP Devices, Enabling HTTPS
 |
UPC - 745883570799
View all Linksys SPA921 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 21 highlights
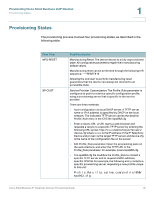
Provisioning Cisco Small Business VoIP Devices Using HTTPS 1 Flow Step SEC-PRV-1 SEC-PRV-2 Step Description Secure Provisioning-Initial Configuration: The initial deviceunique CFG file should be targeted to each IP Telephony Device by compiling the CFG file with the spc --target option. This provides an initial level of encryption that does not require the exchange of keys. The initial device-unique CFG file should reconfigure the profile parameters to enable stronger encryption, by programming a 256-bit encryption key, and pointing to a randomly generated TFTP directory. For example, the CFG file might contain: Profile_Rule [--key $A] tftp.callme.com/profile/$B/ spa962.cfg; GPP_A 8e4ca259...; # 256 bit key GPP_B Gp3sqLn...; # random CFG file path directory Secure Provisioning-Full Configuration: The subsequent profile resync operations retrieve 256-bit encrypted CFG files, which maintain the IP Telephony Device in a state synchronized to the provisioning server. All remaining parameters are configured and maintained through this strongly encrypted profile. The encryption key and random directory location can be changed periodically for extra security. Using HTTPS The IP Telephony Device provides a reliable and secure provisioning strategy based on HTTPS requests from the device to the provisioning server. Both a server certificate and a client certificate a used to authenticate the IP Telephony Device to the server and the server to the IP Telephony Device. To use HTTPS, you must generate a Certificate Signing Request (CSR) and submit it to Cisco. Cisco generates a certificate for installation on the provisioning server. The IP Telephony Device accepts the certificate when it seeks to establish an HTTPS connection with the provisioning server. This procedure is described in the "Enabling HTTPS" section on page 26. Cisco Small Business IP Telephony Devices Provisioning Guide 19