Netgear WGR614v5 WGR614v5 Reference Manual - Page 22
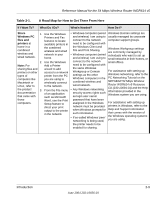
Table 2-1., A Road Map for How to Get There From Here, If I Want To?, What Do I Do?, What's Needed? - hack
 |
View all Netgear WGR614v5 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 22 highlights
Reference Manual for the 54 Mbps Wireless Router WGR614 v5 exposes them to the inherent complexity of networking. General networking concepts, setup, and maintenance can be difficult to understand. In addition, wireless technology adds issues, such as range, interference, signal quality, and security to the picture. To help overcome potential barriers to successfully using home networks, the table below identifies how to accomplish such things as connecting to a wireless network, assuring appropriate security measures are taken, browsing the Internet through your wireless connection, exchanging files with other computers and using printers in the combined wireless and wired network. Table 2-1. A Road Map for How to Get There From Here If I Want To? What Do I Do? What's Needed? How Do I? Set up a wireless network 1. Set up the 54 Mbps Wireless Router WGR614 v5 2. Identify the wireless network name (SSID) and, if used, the wireless security settings. 3. Set up the wireless computers with the settings from step 1. • A wireless network • A computer within the operating range of the wireless network. For guidelines about the range of wireless networks, see "Observe Performance, Placement, and Range Guidelines" on page 4-1". To set up the WGR614 v5, see Chapter 3, "Connecting the Router to the Internet" and follow the instructions provided. To learn about wireless networking technology, see Appendix 4, "Wireless Configuration" for a general introduction. Protect my wireless connection from snooping, hacking, or information theft. 1. Assure that the wireless network has security features enabled. • A wireless network WEP or WPA security enabled. • Wireless networking equipment that supports To learn about wireless networking security, see "Wireless Networking Basics" on page D-1. 2. Configure my WGR614 v5 with WEP or WPA, such as the WGR614 v5. To use WEP security features, the security settings see "Implement Appropriate of the wireless Wireless Security" on page 4-2" network. and configure your WGR614 v5 3. Use Windows accordingly. security features. Note: Secure Internet sites such as banks and online merchants use encryption security built into browsers like Internet Explorer and Netscape. Any wireless networking security features you might implement are in addition to those already in place on secure Internet sites. 2-8 Introduction June 2004 202-10036-01