TP-Link T1700X-16TS T1700X-16TSUN V1 User Guide - Page 41
Access Security
 |
View all TP-Link T1700X-16TS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 41 highlights
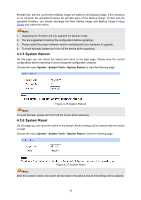
4.4 Access Security Access Security provides different security measures for the remote login so as to enhance the configuration management security. It can be implemented on Access Control, HTTP Config, HTTPS Config, SSH Config and Telnet Config pages. 4.4.1 Access Control On this page you can control the users logging on to the Web management page to enhance the configuration management security. The definitions of Admin and Guest refer to 4.2 User Management. Choose the menu System→Access Security→Access Control to load the following page. Figure 4-18 Access Control The following entries are displayed on this screen: Access Control Config Control Mode: Access Interface: Select the control mode for users to log on to the switch. Disable: Select to disable Access Control function. IP-based: Select this option to limit the IP-range of the users for access. MAC-based: Select this option to limit the MAC Address of the users for access. Port-based: Select this option to limit the ports for access. Select the interface for access control to apply. IP Address & Mask: These fields is available to configure only when IP-based mode is selected. Only the users within the IP-range you set here are allowed for login. 30