ZyXEL N220 User Guide - Page 38
Before You Begin, 3.2 Wireless LAN Overview
 |
View all ZyXEL N220 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
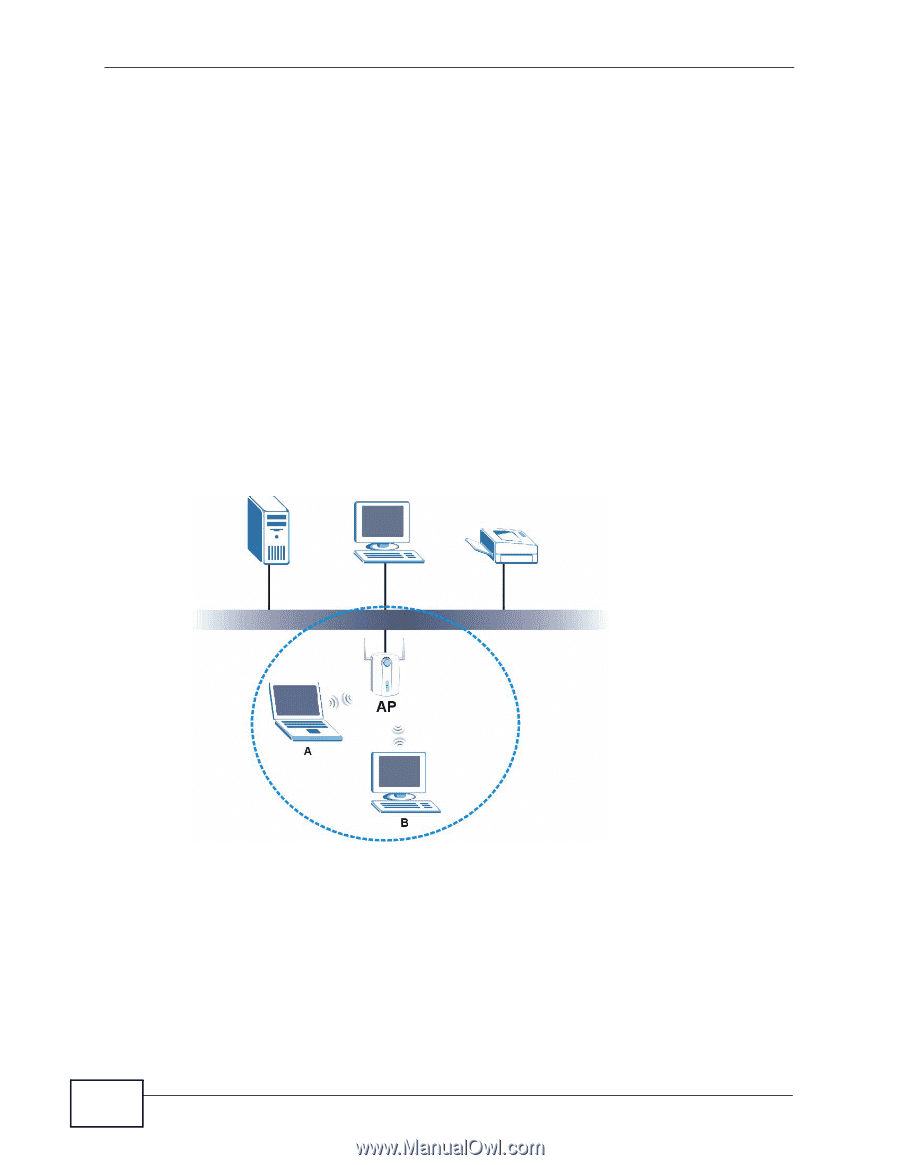
Chapter 3 Wireless LANs Encryption The process of taking data and encoding it, usually using a mathematical formula, so that it becomes unreadable unless decrypted with the proper code or pass phrase. 3.1.3 Before You Begin • You should have valid login information for an existing network Access Point, otherwise you may not be able to make a network connection right away. 3.2 Wireless LAN Overview The following figure provides an example of a wireless network with an AP. See Figure 3 on page 20 for an Ad Hoc network example. Figure 22 Example of a Wireless Network The wireless network is the part in the blue circle. In this wireless network, devices A and B are called wireless clients. The wireless clients use the access point (AP) to interact with other devices (such as the printer) or with the Internet Every wireless network must follow these basic guidelines. • Every device in the same wireless network must use the same SSID. The SSID is the name of the wireless network. It stands for Service Set IDentity. 38 N220 User's Guide