ZyXEL N220 User Guide - Page 50
Before You Begin, 4.2 ZyXEL Utility Screen Summary
 |
View all ZyXEL N220 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 50 highlights
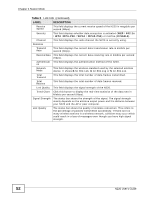
Chapter 4 Station Mode Message Integrity Check (MIC) and IEEE 802.1x. WPA uses Advanced Encryption Standard (AES) in the Counter mode with Cipher block chaining Message authentication code Protocol (CCMP) to offer stronger encryption than TKIP. WPA applies IEEE 802.1x and Extensible Authentication Protocol (EAP) to authenticate wireless clients using an external RADIUS database. The WPA protocol affords users with vastly stronger security than the WEP protocol. It comes in two different varieties: WPA and WPA2. Always try to use WPA2 as it implements the full version of the security standard while WPA does not. Pre-Shared Key (PSK) A pre-shared key is a password shared between the server and the client that unlocks the algorithm used to encrypt the data traffic between them. Without the proper password, the client and the server cannot communicate. Extensible Authentication Protocol (EAP) An enhanced security framework designed to improve an existing security protocol, such as WPA-PSK or WPA2-PSK. 4.1.3 Before You Begin • Make sure the ZyXEL utility is already installed. See the Quick Start Guide for more. 4.2 ZyXEL Utility Screen Summary This section describes the ZyXEL utility screens. Figure 28 ZyXEL Utility Menu Summary The following table describes the menus. Table 4 ZyXEL Utility Menu Summary TAB DESCRIPTION Link Info Use this screen to see your current connection status, configuration and data rate statistics. Site Survey Use this screen to: • scan for a wireless network. • configure wireless security (if activated on the selected network). • connect to a wireless network. 50 N220 User's Guide