Cisco WRVS4400N Administration Guide - Page 136
IPS > Configuration, Enable, Disable, TELNET, Browse, Signature Update, Update, STEP 1 - ips signature
 |
UPC - 745883574797
View all Cisco WRVS4400N manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 136 highlights
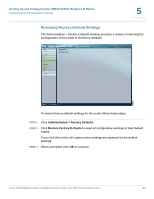
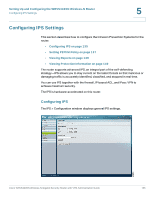
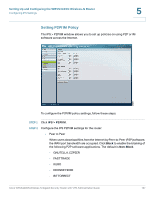
Setting Up and Configuring the WRVS4400N Wireless-N Router Configuring IPS Settings 5 To configure general IPS settings: STEP 1 Click IPS > Configuration. STEP 2 In the IPS Function field, click Enable. STEP 3 In the Anomaly Detection section, configure the detection settings: • HTTP-Web attacks use weaknesses on HTTP protocol to trigger the buffer overflow on Web servers. The default is Disable. • FTP-FTP attacks use weaknesses on FTP protocol to generate illegal FTP commands to the FTP server. The default is Disable. • TELNET-Telnet attacks use weakness on TELNET protocol to execute illegal commands on the TELNET server. The default is Disable. • RPC-Remote Procedure Call allows attackers to issue illegal commands to be executed on RPC server. The default is Disable STEP 4 To protect your local network from the latest Internet threats, upgrade the IPS signature file regularly: a. Download the signature file from www.cisco.com to your personal computer. b. Click Browse to locate the signature file. Alternatively, enter the path to the file in the Signature Update field c. Click Update. STEP 5 Click Save. Cisco WRVS4400N Wireless-N Gigabit Security Router with VPN Administration Guide 136