Dell PowerVault DL4000 Dell PowerVault DL4000 Backup To Disk Appliance - Power - Page 18
Replication, Replication, Read-Match-Write Replication
 |
View all Dell PowerVault DL4000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 18 highlights
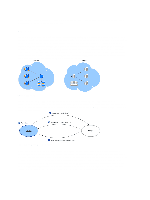
In replication scenarios, AppAssure 5 uses SSL 3.0 to secure the connections between the two cores in a replication topology to prevent eavesdropping and tampering. Replication Replication is the process of copying recovery points and transmitting them to a secondary location for the purpose of disaster recovery. The process requires a paired source-target relationship between two cores. Replication is managed on a per-protected-machine basis; meaning, backup snapshots of a protected machine are replicated to the target replica core. When replication is set up, the source core asynchronously and continuously transmits the incremental snapshot data to the target core. You can configure this outbound replication to your company's own data center or remote disaster recovery site (that is, a "self-managed" target core) or to a managed service provider (MSP) providing off-site backup and disaster recovery services. When you replicate to an MSP, you can use built-in workflows that let you request connections and receive automatic feedback notifications. Figure 4. Replication Replication is self-optimizing with a unique Read-Match-Write (RMW) algorithm that is tightly coupled with deduplication. With RMW replication, the source and target replication service matches keys before transferring data and then replicates only the compressed, encrypted, deduplicated data across the WAN, resulting in a 10x reduction in bandwidth requirements. Figure 5. Read-Match-Write Replication Replication begins with seeding, the initial transfer of deduplicated base images and incremental snapshots of the protected agents, which can add up to hundreds or thousands of gigabytes of data. Initial replication can be seeded to the target core using external media. This is typically useful for large sets of data or sites with slow links. The data in the seeding archive is compressed, encrypted and deduplicated. If the total size of the archive is larger than the space available on the removable media, the archive can span across multiple devices based on the available space on the media. During the seeding process, the incremental recovery points replicate to the target site. After the target core consumes the seeding archive, the newly replicated incremental recovery points automatically synchronize. 18