Dell PowerVault TL4000 Dell Model TL24iSCSIxSAS 1Gb iSCSI to SAS - User's G - Page 51
Adding an iSCSI Target
 |
View all Dell PowerVault TL4000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 51 highlights
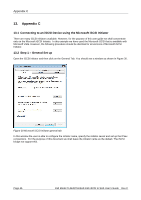
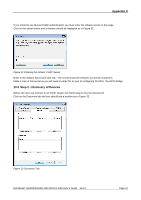
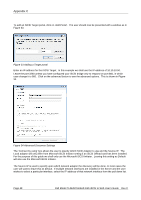
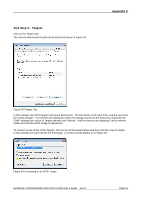
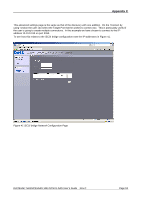
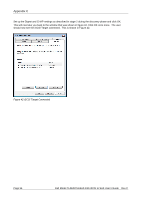
Appendix C CRC/Checksum settings allow the user to specify whether the discovery is done using Data and/or Header Digests. Unless the iSCSI device is on a poor quality network where data corruption is likely, it is recommended then Header and Data Digests are left disabled, as performance will be affected. If the iSCSI bridge has had CHAP enabled, or the user wishes to authenticate the iSCSI bridge, click on the checkbox 'CHAP login information' to enable CHAP. Now enter the username and target secret that was configured on the iSCSI bridge. If the user wishes to authenticate the iSCSI bridge, select 'Perform mutual authentication'. Note: For mutual CHAP to be performed, the Initiator Secret must be set on the general tab, and be the same as the one configured on the iSCSI bridge. The use of RADUS is beyond the scope of this guide. Once the user is satisfied that all advanced options are correct click OK. The user should now see a window as in Figure 35. Figure 35 Adding an iSCSI Target Dell Model TL24iSCSIxSAS 1Gb iSCSI to SAS User's Guide Rev.C Page 49