Netgear WAG102 WAG102 Reference Manual - Page 45
Understanding Security Profiles, If you are using a RADIUS Server, con the RADIUS settings first
 |
UPC - 606449028799
View all Netgear WAG102 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 45 highlights
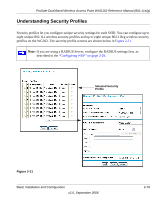
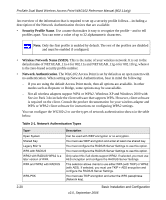
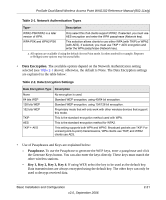
ProSafe Dual Band Wireless Access Point WAG102 Reference Manual (802.11a/g) Understanding Security Profiles Security profiles let you configure unique security settings for each SSID. You can configure up to eight unique 802.11a wireless security profiles and up to eight unique 802.11b/g wireless security profiles on the WG302. The security profile screens are shown below in Figure 2-11. Note: If you are using a RADIUS Server, configure the RADIUS settings first, as described in the "Configuring WEP" on page 2-29. Selected Security Profile Figure 2-11 Basic Installation and Configuration v2.0, September 2006 2-19

ProSafe Dual Band Wireless Access Point WAG102 Reference Manual (802.11a/g)
Basic Installation and Configuration
2-19
v2.0, September 2006
Understanding Security Profiles
Security profiles let you configure unique security settings for each SSID. You can configure up to
eight unique 802.11a wireless security profiles and up to eight unique 802.11b/g wireless security
profiles on the WG302. The security profile screens are shown below in
Figure 2-11
.
Note:
If you are using a RADIUS Server, configure the RADIUS settings first, as
described in the
“Configuring WEP” on page 2-29
.
Figure 2-11
Selected Security
Profile