HP StorageWorks 2/16V HP StorageWorks Fabric OS 5.X Procedures User Guide (AA- - Page 39
Configuring standard security features, Secure protocols, Table 4 Secure protocol support
 |
View all HP StorageWorks 2/16V manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 39 highlights
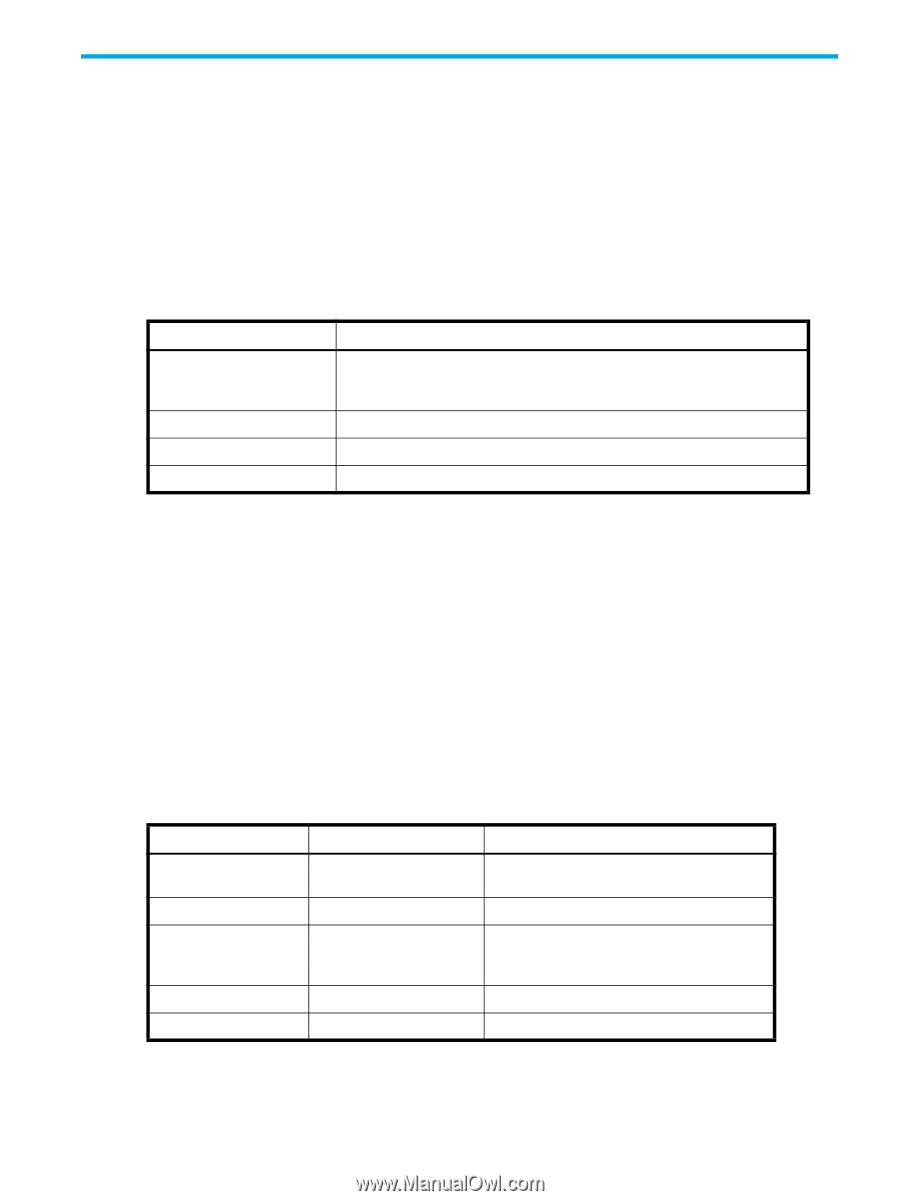
3 Configuring standard security features This chapter provides information and procedures for configuring standard Fabric OS security features such as account and password management. Additional security features are available when secure mode is enabled. For information about licensed security features available in Secure Fabric OS, see the HP StorageWorks Secure Fabric OS administrator guide. Secure protocols Fabric OS supports the secure protocols shown in Table 4. T, able 4 Secure protocol support Protocol Description Secure Sockets Layer (SSL) HTTPS Secure File Copy (scp) SNMPv3 Supports SSLv3, 128-bit encryption by default. Fabric OS uses SSL to support HTTPS. A certificate must be generated and installed on each switch to enable SSL. Advanced Web Tools supports the use of HTTPS. Configuration upload and download support the use of scp. SNMPv1 is also supported. SNMP is a standard method for monitoring and managing network devices. Using SNMP components, you can program tools to view, browse, and manipulate HP StorageWorks switch variables and set up enterprise-level management processes. Every HP StorageWorks switch carries an SNMP agent and Management Information Base (MIB). The agent accesses MIB information about a device and makes it available to a network manager station. You can manipulate information of your choice by trapping MIB elements using the Fabric OS CLI, Advanced Web Tools, or Fabric Manager. The SNMP Access Control List (ACL) provides a way for you to restrict SNMP get and set operations to certain hosts and IP addresses. This is used for enhanced management security in the SAN. For details on HP StorageWorks MIB files, naming conventions, loading instructions, and information about using the HP SNMP agent, see the HP StorageWorks Fabric OS 5.x MIB reference guide. Table 5 describes additional software or certificates that you must obtain to deploy secure protocols. Table 5 Items needed to deploy secure protocols Protocol Host side Switch side Secure telnet (sectelnet) Secure Shell (SSH) HTTPS Secure File Copy (scp) SNMPv3, SNMPv1 Sectelnet client SSH client No requirement on host side except a browser that supports HTTPS SSH daemon, scp server None License not required, but a switch certificate issued by HP is required None Switch IP certificate for SSL None None The security protocols are designed with the four main usage cases described in Table 6. Fabric OS 5.x administrator guide 39