Cisco 7921G Administration Guide - Page 24
Understanding Security Profiles, SETTINGS > Device, Information > Security > Security Mode - wireless controller configuration
 |
UPC - 882658123108
View all Cisco 7921G manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 24 highlights
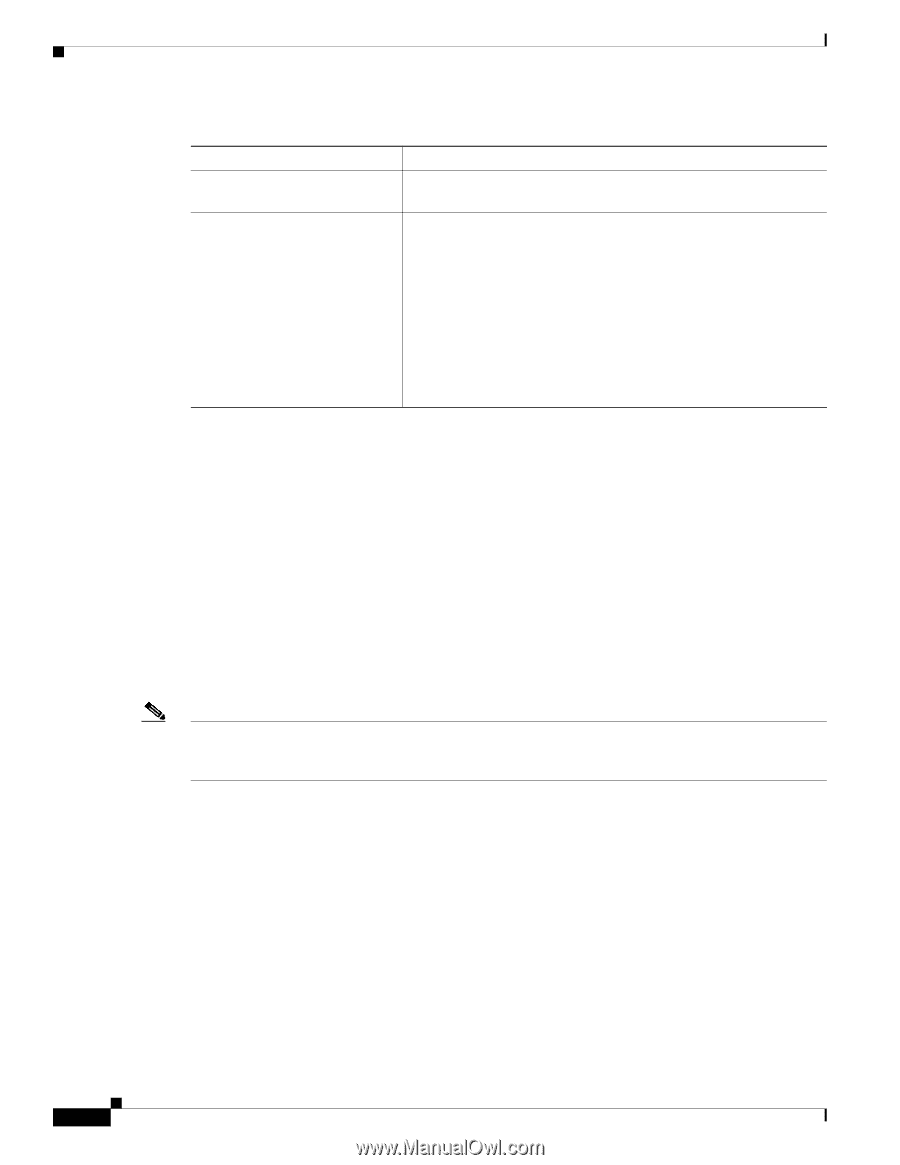
Understanding Security Features for Cisco Unified IP Phones Chapter 1 Overview of the Cisco Unified Wireless IP Phone 7921G Table 1-2 Overview of Security Features (continued) Feature Optional disabling of the web server functionality for a phone Phone hardening Description You can prevent access to a phone's web page, which displays a variety of operational statistics for the phone. Additional security options, which you control from Cisco Unified Communications Manager Administration: • Disabling Gratuitous ARP (GARP) • Disabling access to the Setting menus • Disabling access to web pages for a phone Note You can view current settings for the GARP Enabled, and Web Access options by looking at the phone's Device Information menu. For more information, see the "Viewing Security Information" section on page 8-1. Related Topics • Understanding Security Profiles, page 1-10 • Identifying Encrypted and Authenticated Phone Calls, page 1-11 • Viewing Device Information, page 8-4 • Security Restrictions, page 1-11 Understanding Security Profiles A security profile defines whether a phone is non-secure, authenticated, or encrypted and associated with every Cisco Unified IP Phone that is supported by Cisco Unified Communications Manager Administration. For information about configuring the security profile and applying the profile to the phone, refer to Cisco Unified Communications Manager Security Guide. Note Security is configured on each Cisco Unified IP Phone. For more information about configuring security, refer to Cisco Unified CallManager Security Guide at http://www.cisco.com/en/US/products/sw/voicesw/ps556/prod_maintenance_guides_list.html. To view the security mode that is set for the phone, from the phone screen, choose SETTINGS > Device Information > Security > Security Mode. For more information, see the "Viewing Security Information" section on page 8-1. Related Topics • Identifying Encrypted and Authenticated Phone Calls, page 1-11 • Viewing Device Information, page 8-4 • Security Restrictions, page 1-11 1-10 Cisco Unified Wireless IP Phone 7921G Administration Guide for Cisco Unified Communications Manager Release 7.0 OL-15985-01