Cisco CISCO1401 Software Guide - Page 61
Defining AAA Server Groups
 |
UPC - 746320202785
View all Cisco CISCO1401 manuals
Add to My Manuals
Save this manual to your list of manuals |
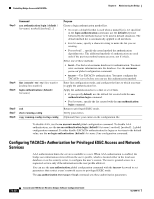
Page 61 highlights
Chapter 5 Administering the Bridge Controlling Bridge Access with RADIUS Step 3 Command aaa authentication login {default | list-name} method1 [method2...] Step 4 Step 5 line [console | tty | vty] line-number [ending-line-number] login authentication {default | list-name} Step 6 Step 7 Step 8 end show running-config copy running-config startup-config Purpose Create a login authentication method list. • To create a default list that is used when a named list is not specified in the login authentication command, use the default keyword followed by the methods that are to be used in default situations. The default method list is automatically applied to all interfaces. • For list-name, specify a character string to name the list you are creating. • For method1..., specify the actual method the authentication algorithm tries. The additional methods of authentication are used only if the previous method returns an error, not if it fails. Select one of these methods: • local-Use the local username database for authentication. You must enter username information in the database. Use the username password global configuration command. • radius-Use RADIUS authentication. You must configure the RADIUS server before you can use this authentication method. For more information, see the "Identifying the RADIUS Server Host" section on page 11-4. Enter line configuration mode, and configure the lines to which you want to apply the authentication list. Apply the authentication list to a line or set of lines. • If you specify default, use the default list created with the aaa authentication login command. • For list-name, specify the list created with the aaa authentication login command. Return to privileged EXEC mode. Verify your entries. (Optional) Save your entries in the configuration file. To disable AAA, use the no aaa new-model global configuration command. To disable AAA authentication, use the no aaa authentication login {default | list-name} method1 [method2...] global configuration command. To either disable RADIUS authentication for logins or to return to the default value, use the no login authentication {default | list-name} line configuration command. Defining AAA Server Groups You can configure the bridge to use AAA server groups to group existing server hosts for authentication. You select a subset of the configured server hosts and use them for a particular service. The server group is used with a global server-host list, which lists the IP addresses of the selected server hosts. Server groups also can include multiple host entries for the same server if each entry has a unique identifier (the combination of the IP address and UDP port number), allowing different ports to be individually defined as RADIUS hosts providing a specific AAA service. If you configure two different host entries on the same RADIUS server for the same service (such as accounting), the second configured host entry acts as a fail-over backup to the first one. OL-4059-01 Cisco Aironet 1400 Series Wireless Bridges Software Configuration Guide 5-9