HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 10
Too Easy: The Repeater
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 10 highlights
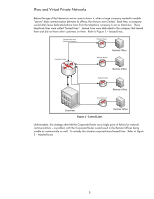
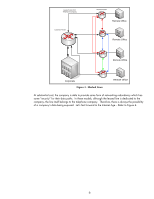
C Figure 7 - Network Model As we can see, the room is secured, but the network attached to the room is not. In addition, although the MFP has been configured to use cryptographic management protocols and has strong passwords, the printing and imaging protocols are unprotected. Jane will use this to her advantage. We'll review five different and mutually exclusive ways in which Jane could have obtained the data. Note: This section and the "Too Easy" sections that follow are focused on printing and imaging. However, the techniques used are applicable to any service running on the network, such as the Domain Name System, Windows Internet Naming Service, Dynamic Host Configuration Protocol, Email, Web Servers, etc... These are not specific printing and imaging vulnerabilities but general TCP/IP protocol vulnerabilities and Ethernet switch vulnerabilities. Too Easy: The Repeater Back in the day when there were no cell phones, homes typically had one phone line. Many a suspicious parent would use this to their advantage. Whenever one of their wild teenagers happened to go to their bedroom to take a phone call, hoping for some privacy, the suspicious parent would listen to their conversations by secretly picking up a telephone somewhere else in the house. The parent was able to listen to their teenager's conversation because all the telephones in the house were connected to the same telephone line. One thing a teenager could do would be to ask for his or her own telephone line to the house, usually under the guise that they would pay for their own bill. Usually this second phone line is installed directly to their bedroom. One ramification of that second phone line is that the parent could no longer listen in from their main telephone line. When a house has a single phone line and multiple phones, it is acting like an Ethernet Hub or as it is sometimes called, an Ethernet Repeater. Refer to Figure 8 - Ethernet Repeater. 10