HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 47
Microsoft Desktops and Laptops running Windows XP/Vista: The most common platforms
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 47 highlights
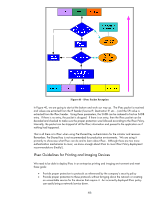
• Provide proper protection to these protocols without causing unreasonable support costs over a non-IPsec protected network. Deploying IPsec really means deploying an IPsec policy - a set of rules for how traffic is to be protected. It would be easier if all devices could simply protect all traffic with IPsec. Unfortunately, that is not a practical choice in most situations. Many times, special considerations must be made that results in differing rule sets on differing device types. A mismatch in the set of rules between differing device types that need to communicate often means that those devices cannot communicate. While there are options to avoid these types of problems, more often than not, they compromise on the certainty of securing traffic with IPsec and are vulnerable to IKE denial of service attacks. There are really four types of network devices that come into play regarding IPsec policy for printing and imaging devices: • Microsoft Desktops and Laptops running Windows XP/Vista: The most common platforms for printing in the Enterprise and also the most important to distribute a broad and clean IPsec policy to due to the number of machines that the IPsec policy will affect and the wide variety of networking applications in use. For this whitepaper, we are assuming a client printing directly to an HP device - HP's Universal Printer Driver is a commonly used component in this type of model - rather than using an intermediate Windows Print Server. • HP Jetdirect Printers and MFPs that support IPsec. Second most common platform in use as there are several desktops or laptops for every shared network printer or MFP. • Servers providing common network services - such as DHCP, DNS, WINS, etc... • Microsoft Servers running Windows Server 2003 and Server 2008: Not as commonly found - used for specialty services like Digital Send Software, Managed Print Spooling, Web Jetadmin, OpenView, or an Email server for MFPs. In addition to these device types, there are also traffic types to worry about. Some services rely heavily on broadcast/multicast traffic in various combinations as well as the traditional unicast traffic. Our IPsec policy must consider these situations. Refer to Figure 41 Traffic Types. 47