HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 4
However, to utilize SSL/TLS
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 4 highlights
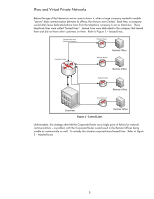
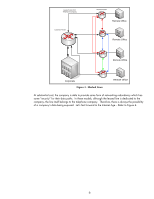
• The user provides credit card information • The user clicks "purchase" The first three items, or the items in red, send data "in the clear" or without being authenticated, confidential, and with limited integrity (i.e., non cryptographic). The last four items, or the items in blue, send data using HTTPS, which in its most popular form is providing one-way authentication, confidentiality, and integrity. Wait a minute - did we say one-way authentication and not mutual authentication? Yes. More importantly, it only provides one-way authentication if you do not get any "Certificate Warning" dialogs, as shown in Figure 1. These dialogs, when appearing in today's HTTPS Internet use-model, are indicative of an authentication problem. If an HTTPS web site on the Internet results in one of these certificate warning dialogs appearing, close the browser and do your shopping elsewhere! You are not able to authenticate the web site and should not be sending over any personal information of any kind. Figure 1 - Authentication Problem with HTTPS Let's assume the web site that you are shopping at is determined to be authentic (i.e., the website is who it says it is). The web site doesn't really care who is using HTTPS via the web browser, therefore client authentication via digital certificates, which would result in mutual authentication, is not done. Imagine a web site that asked you for your digital certificate before you could buy anything. Many people do not have their own digital certificate. How long would that company be in business? The web site does care about providing authentication, confidentiality, and integrity to the data that is being sent to purchase items. This data includes the credit card information. This credit card information provides the company running the web site with the ability to determine if the credit card holder is able to make a purchase - the issuer of the credit card approves or denies the purchase. Once the purchase is approved, the issuer of the credit card is providing protection to both the website and the user regarding fraud. Mutual authentication is provided to the transaction, but only one-way authentication is provided to the communications channel. The HTTPS use model for the Internet has been tremendously successful. However, to utilize SSL/TLS like HTTPS does, the application needs to be modified (e.g., web browser must support HTTPS, certificates, certificate verification, etc...). For many legacy applications in the corporate environment, this modification is not possible. What is needed is for a security protocol to provide authentication, confidentiality, and integrity without the application having to be modified. Here is where IPsec really shines because it can provide just that. Let's take a closer look at what some of the drivers for IPsec were and how this application transparency allowed Virtual Private Networks to appear. 4