HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 34
Publicly Exchanging a Secret
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 34 highlights
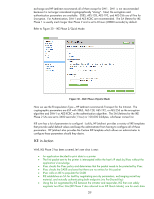
Figure 26 - Publicly Exchanging a Secret Here the Blue PC puts a secret in a box and locks it with the blue lock, then drops the box in the "mail" so to speak and the Green PC receives it. The Green PC puts on a green lock and drops the box back in the mail. The Blue PC removes the blue lock and drops the box back into the mail. The green PC receives it and can now simply remove its green lock and has access to the secret. Think of the Diffie-Hellman group number as the "strength of the locks" used to protect the secret. As an example, DH-Group 2 is "stronger" than DH-Group 1. Both sides need to agree on the strength of the lock before engaging in a DH exchange. That is why the DH group number is part of the proposal 34

34
Figure 26 – Publicly Exchanging a Secret
Here the Blue PC puts a secret in a box and locks it with the blue lock, then drops the box in the
“mail” so to speak and the Green PC receives it. The Green PC puts on a green lock and drops the
box back in the mail.
The Blue PC removes the blue lock and drops the box back into the mail.
The
green PC receives it and can now simply remove its green lock and has access to the secret.
Think of
the Diffie-Hellman group number as the “strength of the locks” used to protect the secret.
As an
example, DH-Group 2 is “stronger” than DH-Group 1.
Both sides need to agree on the strength of
the lock before engaging in a DH exchange.
That is why the DH group number is part of the
proposal