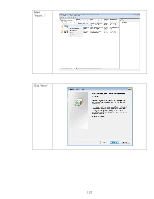
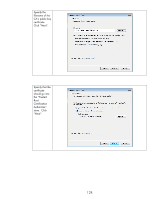
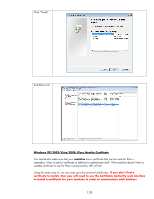
HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 132
Communicate with Jane/DSG.COM Ticket: Service Ticket
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 132 highlights
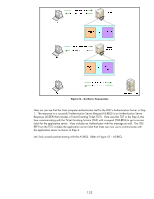
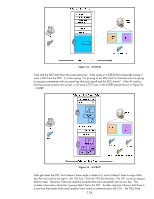
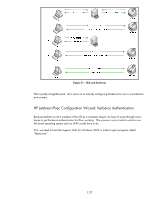
One day, an entrepreneur in the Bay Area of California decided open up a new business. He had surveyed the city and realized that there were many young single male geeks out there. These geeks were very intellectually sharp, but often lived in studio apartments, ate fast food, worked a lot of hours, and most importantly, most of them would stutter and turn red if a lady talked to them. This entrepreneur had figured out that (1) geeks have a lot of money, (2) geeks like technology, (3) geeks are worried about being taken advantage of, and (4) geeks like ladies. He decided to open up a business to help them out. He called this business "Dating Service for Geeks" or DSG. To become a member of DSG, everyone must first pass extensive background checks, pay monthly dues, and have to go through randomized background checks in the future. Once they became a member, they are issued a software program and a password. The software program connected all the members of the DSG to its Authentication Server where their membership in DSG was proven. Once the DSG authenticated the user as being a member of DSG, the DSG would hand out two more items: A Membership Contact Ticket and a Membership Authenticator, both of which were good for about 24 hours; after which, the member of DSG had to use the software program again. Now the entrepreneur really starts to earn his money - he doesn't bother creating a dating web site like other companies do. He simply tells the members of DSG: simply put your membership identity in the text fields of any of the "free" dating services that you currently are a member of. This process allowed our entrepreneur not to invest in web sites and databases and allowed DSG's members to utilize other dating web sites if they wished. Tom, a member of DSG would login to DSG (using the software program) and get his membership contact ticket and his membership authenticator. He would then begin browsing his favorite dating service web site. Tom found someone he liked, a lady named Jane, and Jane had a DSG membership identifier in her profile. It was Jane/DSG.COM. Tom, using the software program to communicate with the DSG Ticket Service, would contact DSG and use his membership contact ticket to obtain a "Communicate with Jane/DSG.COM" ticket and he would provide his membership authenticator to prove he was Tom (and not have to enter his password again). DSG creates a secret key and places it in the "Communicate with Jane/DSG.COM" ticket and also secures it using Tom's membership authenticator and sends it to Tom. DSG has an email service that requires valid "Communicate with X" DSG tickets to work correctly. Using the DSG software program, Tom can send Jane an email for as long as the "Communicate with Jane" ticket is valid. If Jane wasn't a member of DSG or wasn't authenticated to DSG, then the "Communicate with Jane/DSG.COM" ticket couldn't have been issued. Once communication has been established, Tom and Jane know that both of them have gone through DSG's membership process and the background checks associated with it. Let's correlate some of the analogy back to Kerberos terms: • DSG membership id: principal@REALM • DSG Authentication Service: KDC Authentication Service • DSG Ticket Service: KDC Ticket Granting Service • DSG Membership Authenticator: Authenticator • Membership Contact Ticket: Ticket Granting Ticket • "Communicate with Jane/DSG.COM Ticket": Service Ticket Let's look at some diagrams to help cement this Kerberos knowledge. Refer to Figure 52 - Kerberos Transactions. 132