HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 38
transferred using the IKE Phase 1 SA only IKE Phase 2 SA negotiations. - jetdirect reviews
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 38 highlights
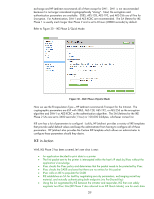
but will be using a different set of keys for sending data than for receiving data. If you are ever debugging IPsec issues, knowing that IPsec has two SAs and not just one will become important. Otherwise, don't worry about it. Why would IKE Phase 2 allow me to select DH Groups again? Didn't I already do that? The reason is "Perfect Forward Secrecy" or PFS. The secret material in the IKE Phase 1 SA is used to generate the keying material in the IPsec SAs. Therefore, if this keying material is somehow compromised in IKE Phase1, then the IPsec SAs can also be compromised. PFS allows for separate keying material to be used anytime an IPsec SA needs to be created. This configuration requires a DH group selection which could be the same value as IKE Phase 1 (e.g., DH-2) or it could be different (e.g., DH-5). Although the DH groups could be configured the same between Phase 1 and Phase 2, the exchanges are different and different values are used respectively. PFS is optional and should only be used if the security policy dictates it. What are Security Association Lifetimes? What is the difference between using a time value and using a byte value? Why are they different between Phase 1 and Phase 2? What do they do? The SA Lifetime value determines either (a) how long in seconds an SA should be used or (b) the amount of data an SA should be used to provide confidentiality and authentication before being discarded. In most cases, the more data that is protected by a single set of keys, the more vulnerable that key is to being discovered. The SA lifetimes allow for the administrator to use different keys for data protection on a regular basis. These lifetimes are also flexible enough to say the following: "Protect up to one Gigabyte of data or protect up to eight hours, whichever comes first, with one set of keys". The Lifetime values allow for new keys to be renegotiated by IKE without administrator intervention. Conventionally, the IKE Phase 1 SA is given a longer lifetime than the IKE Phase 2 SAs because there is greater overhead in negotiation an IKE Phase 1 SA and not as much data is transferred using the IKE Phase 1 SA (only IKE Phase 2 SA negotiations). However, all of these values are configurable on the basis of what is needed to comply with a given security policy. For a quick overview of IKE and the configuration of Phase 1 and Phase 2, let's look at the HP Jetdirect advanced configuration screens to review all the configuration parameters. Refer to Figure 29 - IKE Phase 1: Figure 29 - IKE Phase 1 Here we make the selection between Main and Aggressive mode. For HP Jetdirect, we will always recommend that Main Mode be used. The Diffie-Hellman groups are also there for our Phase 1 38