HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 44
IPsec Basics: Receiving an IPsec Protected Packet
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 44 highlights
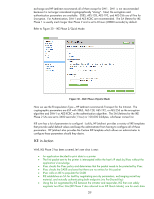
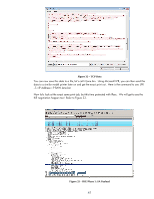
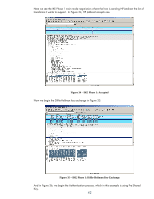
Figure 38 - IPsec Although we know that this is a port 9100 print job, we have no way to tell when IPsec is used, nor can we capture any TCP 9100 packet data that isn't encrypted, play it back, or send it to another printer. IPsec Basics: Receiving an IPsec Protected Packet We can actually cover the last three bullets in this section! Yea! • IPsec checks the IPsec policy and determines that the packet needs to be protected by IPsec • IPsec checks the SADB and sees that there are no entries for this packet • IPsec calls on IKE to populate the SADB • IKE establishes an SA for itself by negotiating security parameters, exchanging secret key material, and mutually authenticating both endpoints (via Pre-Shared Key) • Using the SA negotiated by IKE between the initiator and responder, IKE then can safely negotiate two IPsec SAs (IKE Phase 2 also referred to as IKE Quick Mode), one for each data flow direction, and puts them in the SADB. NOTE: IKE populates the SADB on both the initiator and responder. • IPsec uses these entries to provide IPsec protection to the packet and sends the packet out on the network • The printer receives the IPsec protected packet and checks the SADB for a matching entry based upon the IP addresses and Security Parameters Index (SPI) • IPsec decrypts the packet and then checks the Security Policy to make sure the proper protection was used for the packet • IPsec strips off the IPsec headers and puts the packet back to normal Figure 38 shows the ESP Header close up. 44