HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 36
IKE Phase 2/Quick Mode - jetdirect review
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 36 highlights
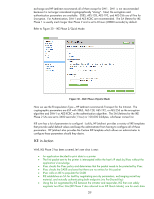
Figure 28 - HP Jetdirect Authentication Method Unfortunately, many pass-phrases like this one are configured once and then never changed. There is no enforcement of a Pre-Shared Key change and Microsoft and HP do not recommend it be deployed in a production environment. Our attacker Jane can begin a brute force search for the Pre-Shared Key password by attempting to communicate to an IPsec node and trying a variety of different PreShared key values. The great benefit of Pre-Shared Key authentication is that it is easy to test and gain experience with IPsec in a lab environment. It is also a good way to explain how IPsec works. Although we have two other forms of Authentication to cover, let's stop here with Pre-Shared Key Authentication and talk about IKE Phase 2 and IPsec SA negotiation. We'll cover Kerberos and Certificate methods of IKE authentication later in the whitepaper. IKE Phase 2/Quick Mode Note: The proposals for IKE Phase 1 concern the establishment of the IKE SA. Therefore, it is possible to use different confidentiality and encryption algorithms for the establishment of the IKE SA than for the establishment of the IPsec SA. In the author's opinion, this flexibility is offset by the amount of confusion it causes. For the purposes of this whitepaper, the algorithms proposed in the IPsec SA establishment phase (Phase 2 or Quick Mode - refer again to Table 2) are the same ones that will be used for IKE SA establishment phase. It is important to review where we are at this point - we have covered a whole lot of information and there is still much more to come! The good news is that the first six entries we have already done, we are on IKE Phase 2, and we have five more entries to cover. Here is our list: • An application decided to print data to a printer • The first packet sent to the printer is intercepted within the host's IP stack by IPsec without the application's knowledge • IPsec checks the IPsec policy and determines that the packet needs to be protected by IPsec • IPsec checks the SADB and sees that there are no entries for this packet • IPsec calls on IKE to populate the SADB 36