HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 5
IPsec and Virtual Private Networks
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 5 highlights
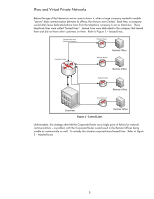
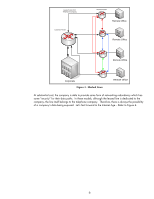
IPsec and Virtual Private Networks Before the age of the Internet as we've come to know it, when a large company wanted to enable "secure" data communication between its offices, the choices were limited. Back then, a company would often lease dedicated phone lines from the telephone company to act as data lines. These telephone lines were called "leased lines". Leased lines were dedicated to the company that leased them and did not have other customers on them. Refer to Figure 2 - Leased Lines. Leased Lines from Telephone Company Remote Router Corporate Router Remote Office Remote Router Remote Office Remote Router Remote Office Remote Router Corporate Figure 2 - Leased Lines Remote Office Unfortunately, this strategy often left the Corporate Router as a single point of failure for network communications - a problem with the Corporate Router would result in the Remote Offices being unable to communicate as well. To remedy this situation required more leased lines. Refer to Figure 3 - Meshed Lines 5