HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 40
Print Job
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 40 highlights
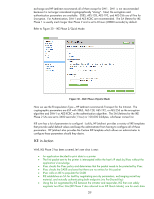
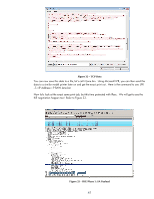
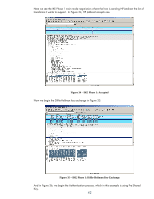
flow direction, and puts them in the SADB. NOTE: IKE populates the SADB on both the initiator and responder. • IPsec uses these entries to provide IPsec protection to the packet and sends the packet out on the network • The printer receives the IPsec protected packet and checks the SADB for a matching entry based upon the IP addresses and Security Parameters Index (SPI) • IPsec decrypts the packet and then checks the Security Policy to make sure the proper protection was used for the packet • IPsec strips off the IPsec headers and puts the packet back to normal Let's use Wireshark to see IKE in action and the actual IPsec protected packet being sent out. First, here is what a non-IPsec protected packet would look like. Remember, the IPsec policy was protecting TCP Port 9100 traffic or normal print data. Our print job is very simple: "Hello, World!" is what we are sending to the printer. Refer to Figure 31 - Print Job Figure 31 - Print Job Using Wireshark, we can see that a TCP connection is setup to port 9100 from IP address 192.168.0.50 to IP address 192.168.0.10. Since the destination port is 9100 and the destination IP address is 192.168.0.10, we can assume that 192.168.0.10 is a printer. Looking at packet 12, we do not see any text with the words "Hello World!" We do not see this information because the data has been processed through a driver and put into a format the printer can understand and process quickly. Do not mistake this for encryption! A person may wonder what you can do with this information. Well, Wireshark allows you to "Follow TCP Stream" as shown in Figure 32. 40