HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 39
IKE in Action
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 39 highlights
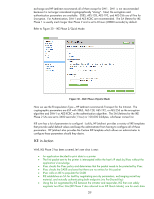
exchange and HP Jetdirect recommends all of them except for DH-1. DH-1 is not recommended because it is no longer considered cryptographically "strong". Next, the encryption and authentication parameters are available. 3DES, AES-128, AES-192, and AES-256 are all fine for Encryption. For Authentication, SHA-1 and AES-XCBC are recommended. The SA lifetime for IKE Phase 1 is usually much longer than Phase 2 and is set to 8 hours (28800 seconds) by default. Refer to Figure 30 - IKE Phase 2/Quick Mode. Figure 30 - IKE Phase 2/Quick Mode Here we see the Encapsulation Type - HP Jetdirect recommends Transport for the Intranet. The cryptographic parameters are ESP with 3DES, AES-128, AES-192, or AES-256 as the encryption algorithm and SHA-1 or AES-XCBC as the authentication algorithm. The SA Lifetimes for the IKE Phase 2 SAs are set to 3600 seconds (1 hour) or 100,000 kilobytes, whichever comes first. IKE sure has a lot of parameters to configure! Luckily, HP Jetdirect provides a variety of IKE templates that provide useful default values and keep the administrator from having to configure all of these parameters. HP Jetdirect also provides the Custom IKE template which allows an administrator to configure these parameters should they desire. IKE in Action Well, IKE Phase 2 has been covered, let's see what is next: • An application decided to print data to a printer • The first packet sent to the printer is intercepted within the host's IP stack by IPsec without the application's knowledge • IPsec checks the IPsec policy and determines that the packet needs to be protected by IPsec • IPsec checks the SADB and sees that there are no entries for this packet • IPsec calls on IKE to populate the SADB • IKE establishes an SA for itself by negotiating security parameters, exchanging secret key material, and mutually authenticating both endpoints (via Pre-Shared Key) • Using the SA negotiated by IKE between the initiator and responder, IKE then can safely negotiate two IPsec SAs (IKE Phase 2 also referred to as IKE Quick Mode), one for each data 39