HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 107
HP Jetdirect and Public Key Certificates, IKE Authentication: Public Key Certificates, The Microsoft
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 107 highlights
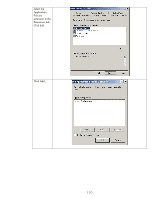
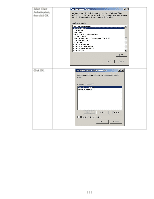
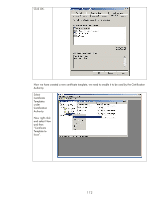
Public Key Infrastructure (PKI) that includes an entire policy around certificates. Because we are discussing IPsec for the Intranet, we will be talking about Microsoft's certificate authorities later on. HP Jetdirect and Public Key Certificates Now that we have covered some basics around certificates, we can talk specifically about Jetdirect. Jetdirect is an embedded system and as a result, has limited storage space for certificates. Jetdirect can store one Identity certificate and one CA certificate. The CA certificate tells Jetdirect which identity certificates should be trusted (i.e., must be signed by that CA) when Jetdirect is receiving a certificate from another entity. Jetdirect's Identity certificate is the certificate that is sent out when another entity requests it. It is important to note that the CA certificate on Jetdirect is configured strictly to provide the trust point for identity certificates that are sent to Jetdirect - the identity certificates received from other entities must be signed by that CA. Since Jetdirect only has one Identity certificate that can be configured, it must be capable of being used in a variety of situations. Jetdirect can act as a client or a server, depending on the protocol being used. For instance, if a web browser is using HTTPS to communicate to Jetdirect, Jetdirect will return its Identity certificate as part of the SSL/TLS negotiation process. In other cases, like LDAPS, Jetdirect will send its Identity certificate for client authentication if required. We do not want to install a Jetdirect Identity certificate that works for IPsec but fails for SSL/TLS. In this whitepaper, we will cover how to create a Jetdirect certificate with the proper attributes to satisfy all the protocols. By default, Jetdirect will create a "self-signed" certificate the first time it is powered on. This certificate is not secure because it has not been signed by a trusted CA. An important step in the security of a Jetdirect product is to replace the default self-signed Identity certificate with one that has been signed by a trusted CA. IKE Authentication: Public Key Certificates How does IPsec use certificates? Well, these certificates only come into play during IKE negotiation and specifically they only affect the Authentication phase in IKE Phase 1. All other things we discussed about IPsec remain the same. During the authentication phase, these public key certificates are exchanged. The following items are verified: • Is the certificate signed by the configured CA? • Does the certificate holder posses the corresponding private key for that certificate? If each certificate passes these tests, then authentication is successful. Otherwise, IKE phase 1 doesn't pass and IPsec communication cannot happen. The Microsoft Certificate Authority Environment Microsoft has an "Enterprise CA" and a "Standalone CA". The Enterprise CA is pretty common among the environments that would potentially use IPsec. Therefore, this whitepaper will focus on the enterprise CA. In order to ensure that the Jetdirect certificates are created correctly, we will need to create a Certificate Template. A certificate template is the guide that controls how the certificates are created. 107