HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 9
Secured MFP - review
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 9 highlights
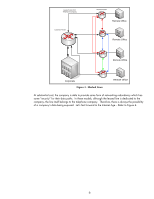
card to be used. In addition, the only electronic digital sending device that the company had was placed in an accessrestricted security room monitored by a camera. Figure 6 - Secured MFP shows the setup: Camera C Open Conference Area C Secure MFP Room Card Access Figure 6 - Secured MFP Because you are paranoid about someone scanning in your data and emailing it or transporting it electronically to the competition, you force the MFP to send all digital information to a server where the data is scanned for watermarked words such as "confidential" or "secret". If any of these words are found, the server quarantines the data until security approves of the electronic data transfer. The room is locked at night and camera logs are archived. The MFP has also been secured by disabling unused protocols, forcing management protocols to use cryptographic protection such as SSL/TLS, and setting strong passwords. One day, one of your top employees, Jane Doe puts in her two week notice, citing medical reasons. Because your design breakthrough has left you slightly suspicious of everyone, you review the security camera logs and the confidential document logs and determine all is in order in regards to Jane Doe. A few days go by and you are interviewing Jane's replacement, Jill Fawn. Jill, who works for one of your competitors, claims to have seen Jane interviewing at the company she works for and believes she'll start her new job soon. You are shocked as Jane had cited medical reasons for leaving so you believe that she is up to no good. As Jane leaves on her last day, you ask security to conduct a surprise inspection of all of her outgoing possessions in case they belong to your company. The security team discovers a compact disc containing nearly all of the confidential documents related to the graphic design breakthrough! The security team reviews all the document check out logs and the camera logs associated with Jane and determines that Jane never accessed those documents nor did she ever use the MFP! How did Jane get those documents? Note: Many individuals reading the above 'case-study' will probably believe that Jane did something wrong. Legally however, it really depends on the company's security policy. Did the company have a security policy covering the access and use of this type of data? What about 'malicious' software that can be used to redirect data, tamper with data, and capture data? Was this policy communicated clearly and was it easily accessible? How was it enforced? Imagine if Jane took the case to court to legally obtain the documents that were in her possession and your company lost because you hadn't defined a security policy! IPsec is not a replacement for a security policy! Instead, it is a protocol that can be used to be compliant with a company's security policy. Jane didn't check out those documents, she didn't scan them in, and she didn't hack into the MFP over the network. Yet Jane still obtained them. You may think that Jane is an accomplished hacker. She isn't. She was able to accomplish all of this by downloading two free tools from the Internet and some light reading about how to use them. Let's look at Figure 7 and we'll see some more of the network and the open conference area that Jane used. 9