HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 8
The Intranet Threat Model
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 8 highlights
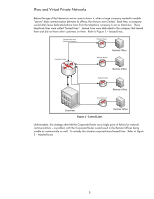
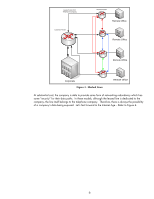
Figure 5 - Internet VPN Age What happens in Figure 5 is that all data communication occurring between the Remote Router and the Corporate Router is provided confidentiality, authentication, and integrity via IPsec. It is like we have been able to create a leased line under our control right through the Internet. Also, the applications that send data from the Corporate Office to the Remote Offices are not aware that security is being used; hence the applications don't have to be modified to work in such an environment. They work transparently over the Intranet and Internet. What data is protected with IPsec depends on the IPsec policy. The IPsec policy is a set of rules which govern what to do with information that comes in and out of the computer system via the network. For example, the Corporate Router in Figure 4 could have an IPsec policy with one rule that was very simple: "protect data being sent to the Remote Router with IPsec". There are a variety of different ways IPsec can protect data. For the purposes of this whitepaper, "protecting data with IPsec" means "protecting data via mutual authentication, integrity, and confidentiality". The Intranet Threat Model What do Virtual Private Networks have to do with printing and imaging? No company is placing their printers on the public Internet (if you thought spam was bad on fax machines....) so is there a point in talking about IPsec for printing & imaging? While it is true most companies don't deploy their printers on the Internet, it is not true that IPsec cannot benefit printing and imaging devices. To best explain the threats that can be present in an Intranet, let's go through an imaginary "case-study". Case Study: Design Breakthrough and Data Protection You are the CEO of a small startup company that has made a major breakthrough in graphics chip design. As you realize that you could be sitting on a gold mine, you begin to worry about the security of your data. All the relevant documents associated with the design breakthrough are kept under lock and key, extensively watermarked, and must be checked out with a security 8