HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 134
AS-REQ, AS-REP
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 134 highlights
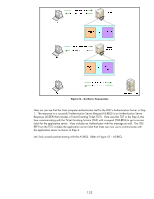
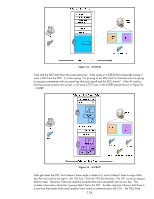
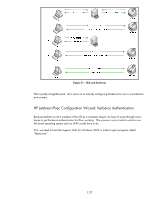
Figure 53 - AS-REQ Vista and the KDC both have the exact same key. Vista sends an AS-REQ that is basically saying "I want a TGT from the TGS. It is also saying "I'm proving to the KDC that I'm Vista because I'm going to encrypt a timestamp with my secret key that only myself and the KDC knows". If the AS verifies that the packet contents are correct, it will send a TGT over in the AS-REP packet shown in Figure 54 - AS-REP. Figure 54 - AS-REP Vista gets back the TGT, but it doesn't know what is inside of it, since it doesn't have a copy of the key that was used to encrypt it - the TGS key. Only the TGS has that key. The TGT is just an opaque blob to Vista. However, Vista can read the contents that were encrypted with its own key. This includes information about the "opaque blob" that is the TGT. Another important thing is that there is a new key that needs to be used anytime Vista wants to communicate to the TGS - the TGS/Vista 134