HP Deskjet 6980 User Guide - Macintosh - Page 29
Wireless security, Infrastructure networks, Ad hoc networks wireless direct-connect - wireless setup mac
 |
UPC - 882780129580
View all HP Deskjet 6980 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 29 highlights
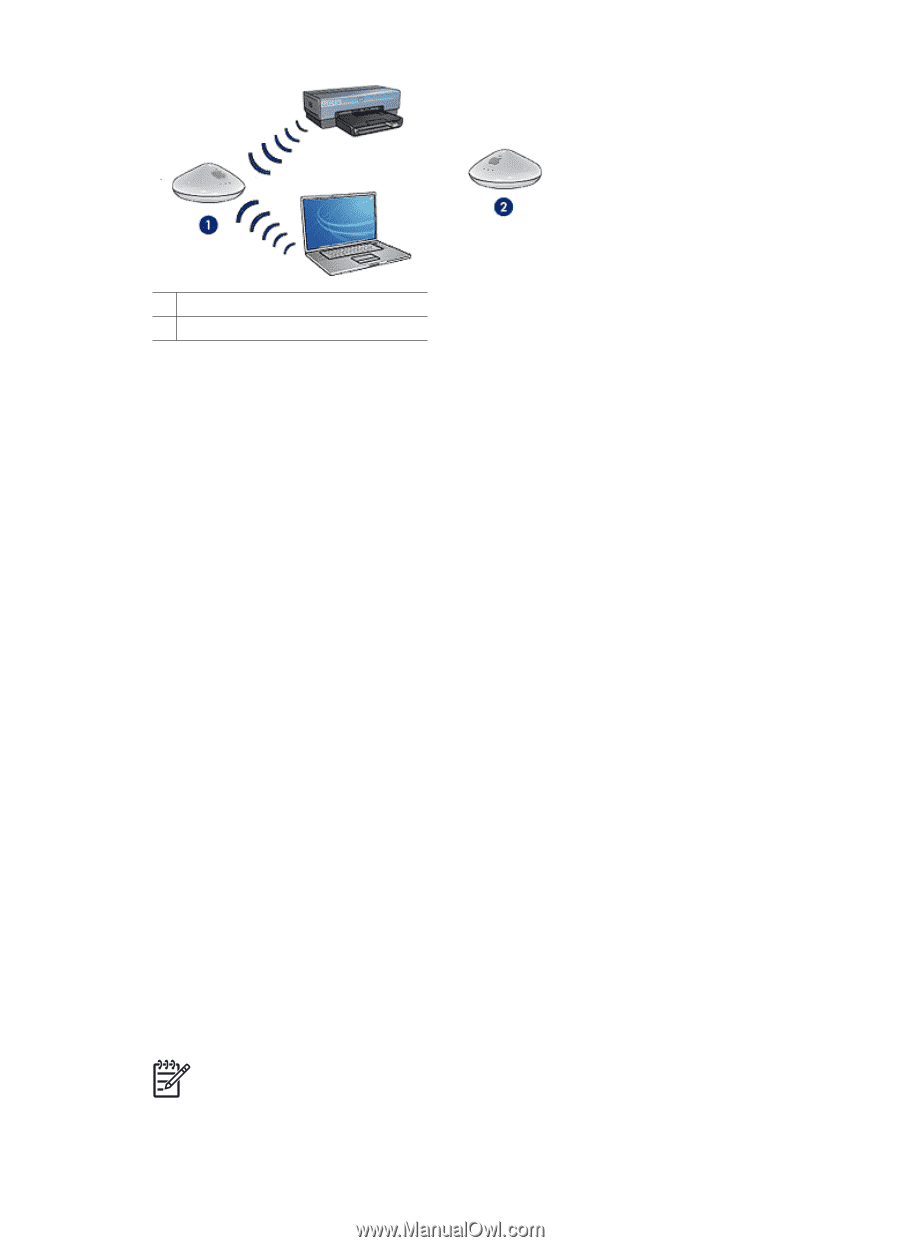
1 Network name equals "network_1" 2 Network name equals "network_2" Wireless security The printer can be configured for several wireless security options depending on the type of wireless network of which the printer is part. Infrastructure networks ● WPA ● WEP ● Open System Ad hoc networks (wireless direct-connect) ● WEP ● Open System For more information about wireless security, see the authentication and encryption page. Add security to the network As with other networks, security for wireless local area networks (WLANs) focuses on access control and privacy. Traditional WLAN security includes the use of Service Set Identifiers (SSIDs), open or shared-key authentication, static Wired Equivalent Privacy (WEP) keys, and optional Media Access Control (MAC) authentication. This combination offers a rudimentary level of access control and privacy. If you are using an access point, you might also employ advanced forms of authentication and encryption on the WLAN, such as the Pre-Shared Key mode of Wi-Fi Protected Access (WPA-PSK). To protect the wireless network, HP strongly suggests you implement a wireless security scheme (either WEP or WPA) during setup, use an antivirus program to protect against computer viruses, and follow basic security rules such as setting strong passwords and not opening unknown attachments. Other network components, including firewalls, intrusion-detection systems, and segmented networks, should also be considered as part of the network design. Note If you decide to add encryption and authentication to the network after installing the printer, change the settings on the printer prior to changing them on other devices on the network. User's guide 27