HP Deskjet 6980 User Guide - Macintosh - Page 31
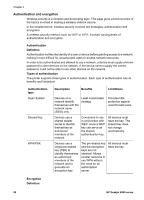
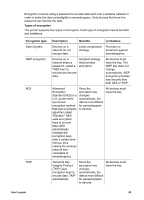
Types of encryption, Encryption type, Description, Benefits, Limitations, U.S. government
 |
UPC - 882780129580
View all HP Deskjet 6980 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
Encryption involves using a password to encode data sent over a wireless network in order to make the data unintelligible to eavesdroppers. Only devices that know the password can decode the data. Types of encryption The printer supports four types of encryption. Each type of encryption has its benefits and limitations. Encryption type Open System WEP encryption AES TKIP Description Benefits Limitations Devices on a network do not encrypt data. Least complicated strategy. Provides no protection against eavesdroppers. Devices on a network share a password, called a "WEP key" to encode and decode data. Simplest strategy that provides encryption. All devices must have the key. The WEP key does not change automatically. WEP encryption provides less security than both AES or TKIP. Advanced Encryption Standard (AES) is a U.S. government sponsored encryption method that uses a complex algorithm called "Rijndael." AES uses encryption keys to encode data. AES automatically changes the encryption keys after a certain time interval, thus making the wireless network less vulnerable to eavesdropping. Since the encryption key changes automatically, the data is more difficult for eavesdroppers to decode. All devices must have the key. Temporal Key Integrity Protocol (TKIP) uses encryption keys to encode data. TKIP automatically Since the encryption key changes automatically, the data is more difficult for eavesdroppers to decode. All devices must have the key. User's guide 29