Netgear WNA1000 WNA1000 User Manual - Page 40
Setting Up WEP Encryption Security, Profile, Network Name SSID
 |
View all Netgear WNA1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 40 highlights
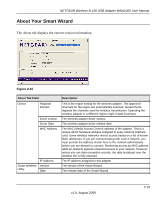
NETGEAR Wireless-N 150 USB Adapter WNA1000 User Manual Setting Up WEP Encryption Security Follow the steps below to configure WEP encryption security: 1. Run the WNA1000 Smart Wizard. a. Make sure that the WNA1000 software is installed and the wireless-N USB adapter is connected to the USB port in your computer. b. Use the icon to open the Smart Wizard. The Settings tab displays. 2. Configure the Security settings. a. In the Profile field, select the profile or type in a profile name. b. In the Network Name (SSID) field, select the network, or enter the SSID. Note: You will not get a wireless network connection unless the network SSID matches exactly what is configured in the access point. c. In the Security section, select WEP. Figure 2-13 2-16 v1.0, August 2009