TP-Link TL-R600VPN TL-R600VPN V1 User Guide - Page 45
Disable All
 |
View all TP-Link TL-R600VPN manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 45 highlights
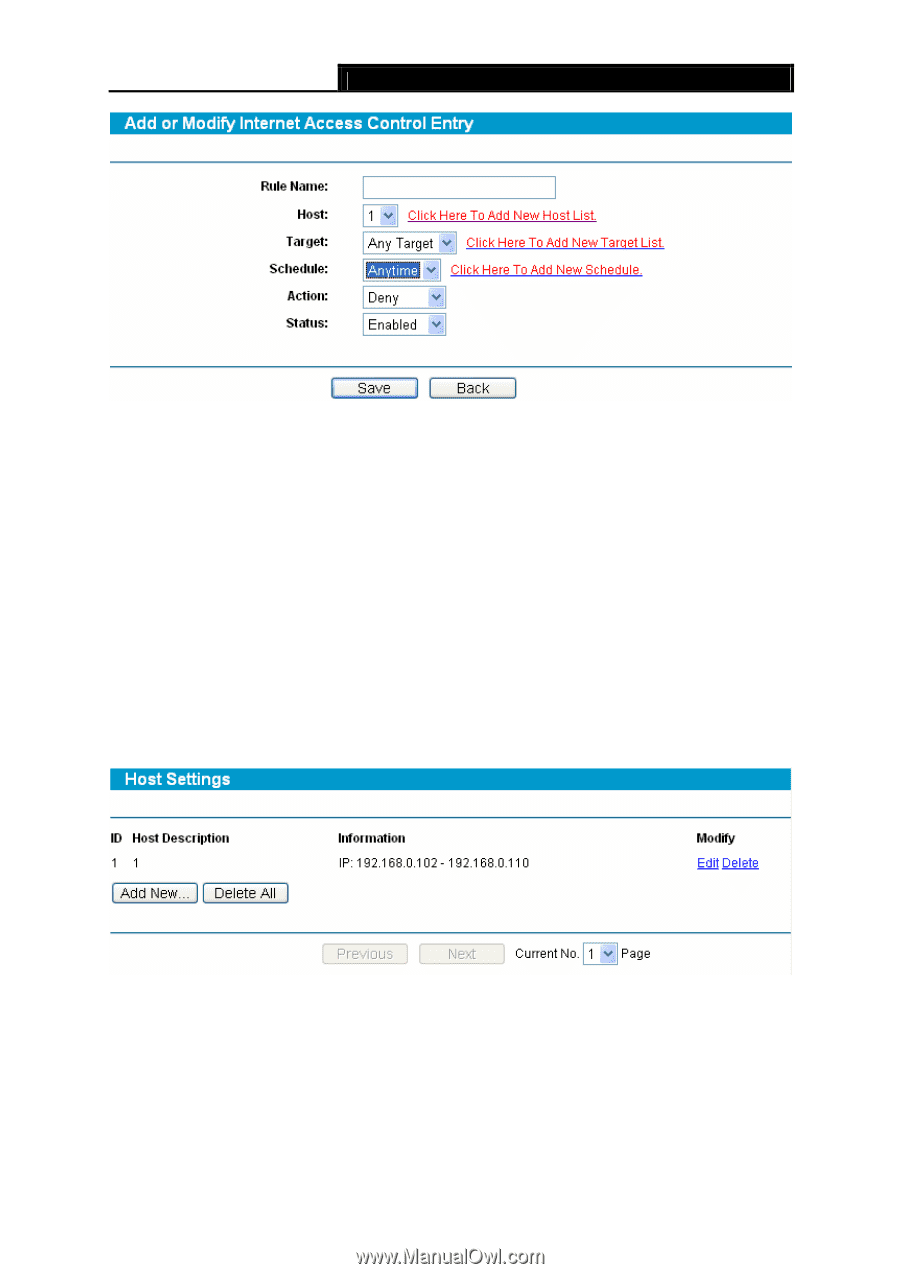
TL-R600VPN SafeStreamTM Gigabit Broadband VPN Router User Guide Step 3: Click the Save button. Figure 4-30 Other configurations for the entries as shown in Figure 4-29: Click the Delete button to delete the entry. Click the Enable All button to enable all the entries. Click the Disable All button to disable all the entries. Click the Delete All button to delete all the entries. Click the Previous button to view the information in the previous screen, click the Next button to view the information in the next screen. 4.7.2 Host Choose menu "Access Control →Host", you can configure Host of the Access Control rule in the next screen (shown in Figure 4-31). Figure 4-31 ¾ Host Description: Displays the description of the host and the description is unique. ¾ Information: Displays the MAC address or IP address of the PCs to which the rule take effect. To add/modify a host for Access Control Rule: Step 1: Click Add New.../Edit shown in Figure 4-31, you will see a new screen shown in Figure 4-32. 39