D-Link DGS-1510-20 User Manual - Page 355
SSH Global Settings, Host Key, Security > SSH > SSH Global Settings
 |
View all D-Link DGS-1510-20 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 355 highlights
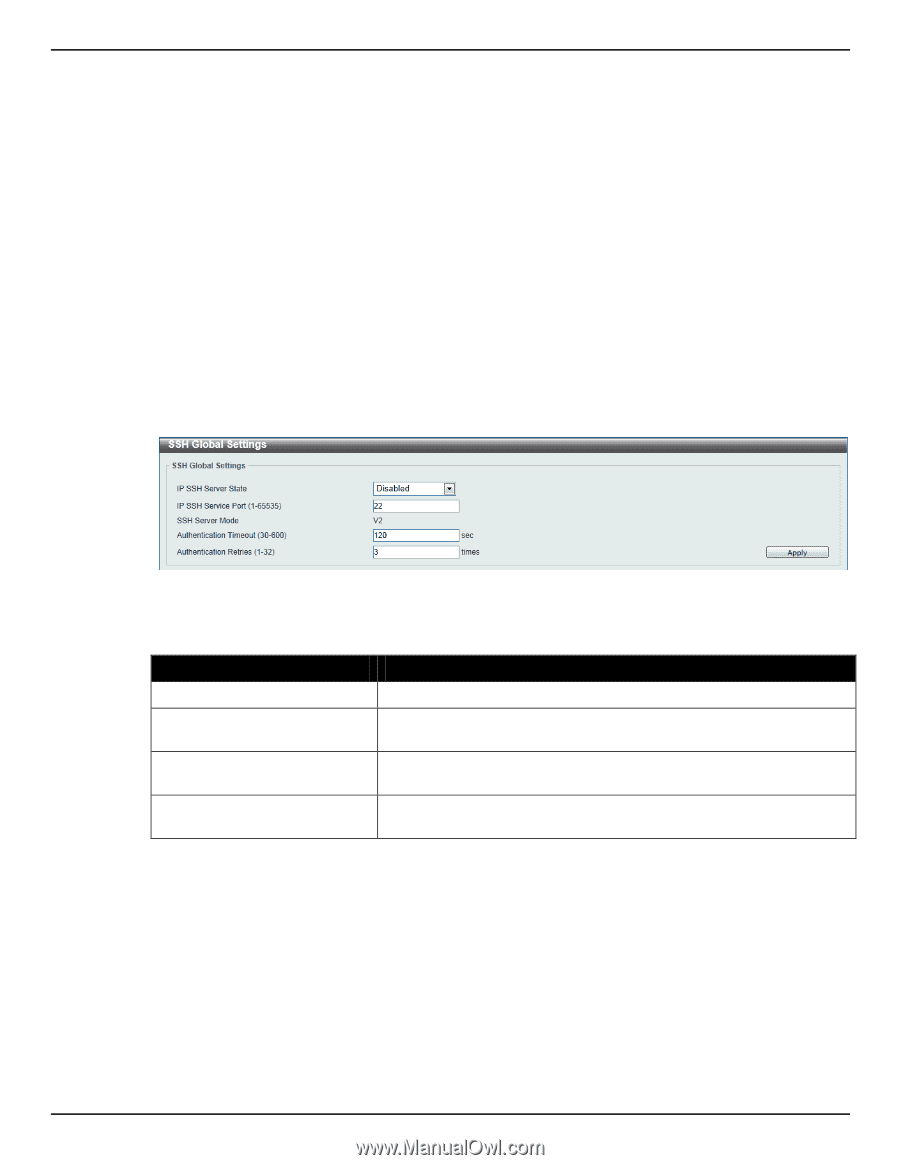
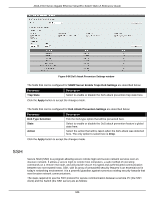
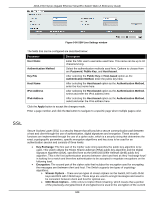
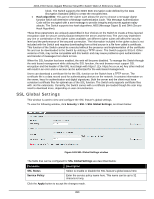
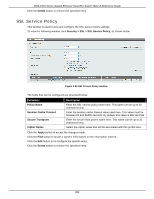
DGS-1510 Series Gigabit Ethernet SmartPro Switch Web UI Reference Guide • Create a user account with admin-level access using the User Accounts window. This is identical to creating any other admin-level User Account on the Switch, including specifying a password. This password is used to logon to the Switch, once a secure communication path has been established using the SSH protocol. • Configure the User Account to use a specified authorization method to identify users that are allowed to establish SSH connections with the Switch using the SSH User Authentication Mode window. There are three choices as to the method SSH will use to authorize the user, which are Host Based, Password, and Public Key. • Configure the encryption algorithm that SSH will use to encrypt and decrypt messages sent between the SSH client and the SSH server, using the SSH Authentication Method and Algorithm Settings window. • Finally, enable SSH on the Switch using the SSH Configuration window. After completing the preceding steps, a SSH Client on a remote PC can be configured to manage the Switch using a secure, in band connection. SSH Global Settings This window is used to view and configure the SSH global settings. To view the following window, click Security > SSH > SSH Global Settings, as shown below: Figure 9-87 SSH Global Settings window The fields that can be configured are described below: Parameter IP SSH Server State IP SSH Service Port Authentication Timeout Authentication Retries Description Select to enable or disable the SSH server's global state. Enter the SSH service port number used here. This value must be between 1 and 65535. By default, this number is 22. Enter the authentication timeout value here. This value must be between 30 and 600 seconds. By default, this value is 120 seconds. Enter the authentication retries value here. This value must be between 1 and 32. By default, this value is 3. Click the Apply button to accept the changes made. Host Key This window is used to view and generate the SSH host key. To view the following window, click Security > SSH > Host Key, as shown below: 347