Netgear FVS318 FVS318 Reference Manual - Page 69
Configuring a SA Using IKE Main Mode, IKE - VPN Settings Main Mode Configuration Menu - throughput
 |
UPC - 606449023381
View all Netgear FVS318 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 69 highlights
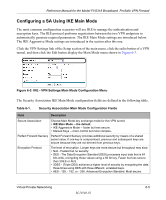
Reference Manual for the Model FVS318 Broadband ProSafe VPN Firewall Configuring a SA Using IKE Main Mode The most common configuration scenarios will use IKE to manage the authentication and encryption keys. The IKE protocol performs negotiations between the two VPN endpoints to automatically generate required parameters. The IKE Main Mode settings are introduced below. The IKE Aggressive Mode settings are introduced in the section after this one. Click the VPN Settings link of the Setup section of the main menu, click the radio button of a VPN tunnel, and then click the Edit button display the Main Mode menu shown in Figure 6-3. Figure 6-3: IKE - VPN Settings Main Mode Configuration Menu The Security Association IKE Main Mode configuration fields are defined in the following table. Table 6-1. Security Association Main Mode Configuration Fields Field Description Secure Association Choose Main Mode key exchange mode for this VPN tunnel: • IKE Main Mode -- the default. • IKE Aggressive Mode -- faster but less secure. • Manual Keys -- more control but more complex. Perfect Forward Secrecy Perfect Forward Secrecy provides additional security by means of a shared secret value. If one key is compromised, previous and subsequent keys are secure because they are not derived from previous keys. Encryption Protocol The level of encryption. Longer keys are more secure but throughput may slow. • Null - Fastest but no security. • DES - The Data Encryption Standard (DES) processes input data that is 64 bits wide, encrypting these values using a 56 bit key. Faster but less secure than 3DES or AES. • 3DES - (Triple DES) achieves a higher level of security by encrypting the data three times using DES with three different, unrelated keys. • AES - 128, - 192, or - 256. Advanced Encryption Standard. Most secure. Virtual Private Networking 6-5 M-10146-01