Netgear FVS318 FVS318 Reference Manual - Page 73
Planning a VPN, Table 6-1., VPN Manual Keys Configuration Fields - software
 |
UPC - 606449023381
View all Netgear FVS318 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 73 highlights
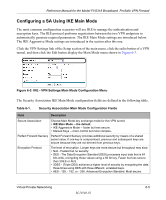
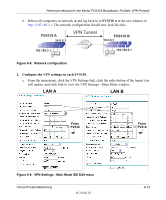
Reference Manual for the Model FVS318 Broadband ProSafe VPN Firewall Table 6-1. VPN Manual Keys Configuration Fields Field Authentication Protocol Authentication Key Key Life IKE Life Time NETBIOS Enable Description Use this drop-down list to select the authentication protocol: • MD5 - the default • SHA1 - more secure Enter the key. • For MD5, the key should be 16 characters. • For SHA-1, the key should be 20 characters. Any value is acceptable, provided the remote VPN endpoint has the same value in its Authentication Protocol Key field. The default is 3600 seconds (one hour). At the end of this time, the connection will drop, the security association will be re-established, and the connection will be reactivated. The default is 28800 seconds (eight hours). If you need to run Microsoft networking functions such as Network Neighborhood, click the NETBIOS Enable check box. Planning a VPN When you set up a VPN, it is helpful to plan the network configuration and record the configuration parameters on a worksheet. These topics are discussed below. Note: NETGEAR will publish additional interoperability scenarios with various gateway and client software products. Look on the NETGEAR web site at www.netgear.com/docs/ for the HTML version of this manual. When you set up a VPN, it is helpful to plan the network configuration and record the configuration parameters on a worksheet. These topics are discussed below and a blank worksheets are provided at the end of this chapter on page 6-31. To set up a VPN connection, you must configure each endpoint with specific identification and connection information describing the other endpoint. You must configure the outbound VPN settings on one end to match the inbound VPN settings on other end, and vice versa. This set of configuration information defines a security association (SA) between the two points. When planning your VPN, you must make a few choices first: Virtual Private Networking 6-9 M-10146-01