TP-Link Archer C2 Archer C2 V1 User Guide 1910010993 - Page 88
Trigger Port
 |
View all TP-Link Archer C2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 88 highlights
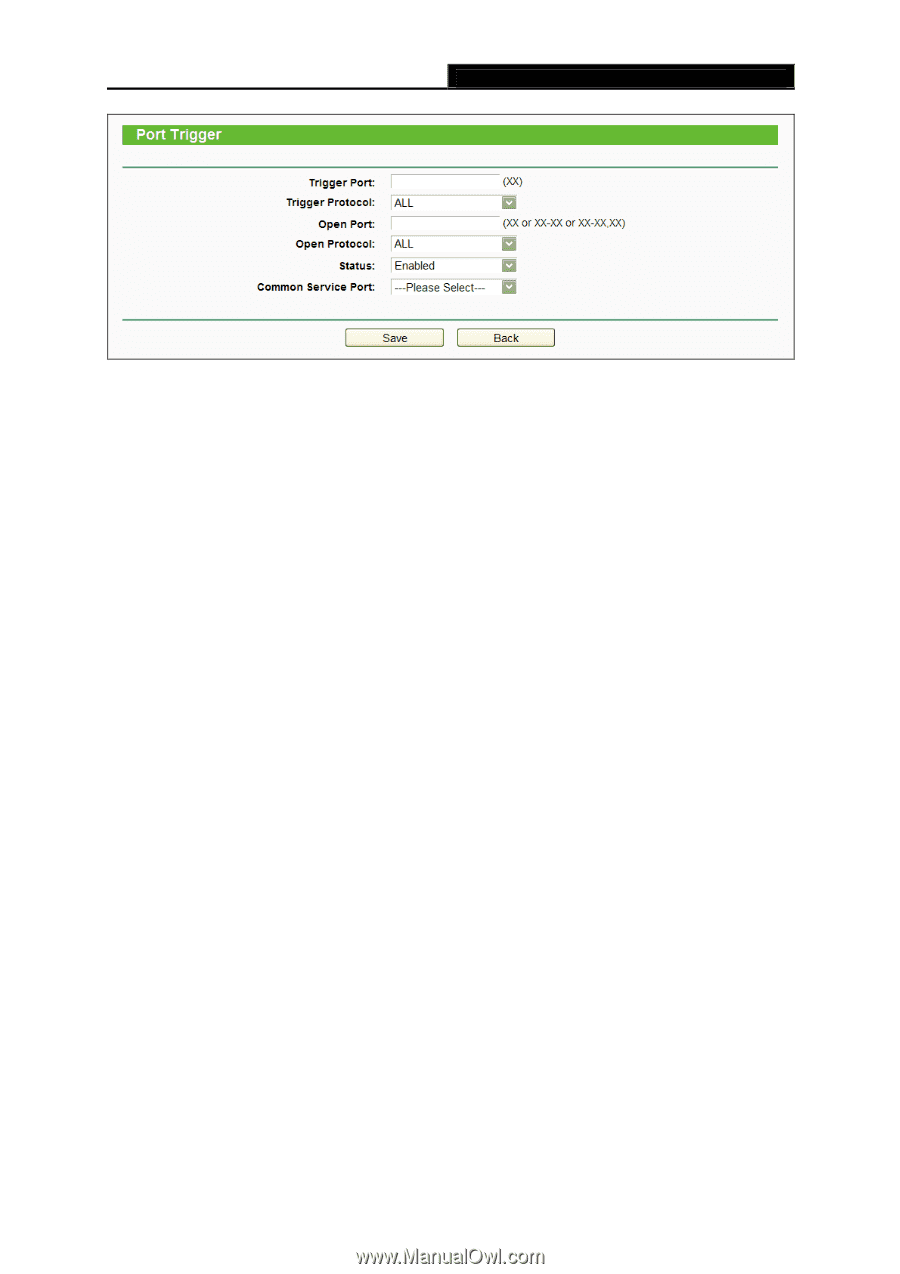
Archer C2 AC750 Wireless Dual Band Gigabit Router Figure 4-65 Add or Modify a Triggering Entry To modify or delete an existing entry: 1. Find the desired entry in the table. 2. Click Edit or Delete as desired on the Edit column. Click the Enable Selected button to make selected entries enabled. Click the Disable Selected button to make selected entries disabled. Click the Delete Selected button to delete selected entries Once the router is configured, the operation is as follows: 1. A local host makes an outgoing connection to an external host using a destination port number defined in the Trigger Port field. 2. The router records this connection, opens the incoming port or ports associated with this entry in the Port Triggering table, and associates them with the local host. 3. When necessary, the external host will be able to connect to the local host using one of the ports defined in the Open Ports field. Note: 1. When the trigger connection is released, the corresponding opened ports will be closed. 2. Each rule can only be used by one host on the LAN at a time. The trigger connection of other hosts on the LAN will be refused. 3. Open Ports ranges cannot overlap each other. 4.12.3 DMZ Choose menu "Forwarding→DMZ", and then you can view and configure DMZ host in the screen (shown in Figure 4-66).The DMZ host feature allows one local host to be exposed to the Internet for a special-purpose service such as Internet gaming or videoconferencing. The router forwards packets of all services to the DMZ host. Any PC whose port is being forwarded must have its - 78 -