HP 635n HP Jetdirect Print Servers - How to Use 802.1X on HP Jetdirect Print S - Page 7
Public Key Infrastructure and Public Key Certificate Basics
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
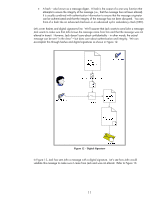
Because Extensible is part of the name of EAP, there are multiple protocols that have been developed under the EAP framework. All HP Jetdirect products supporting 802.1X also support Protected EAP or PEAP. Many HP Jetdirect products also support EAP-Transport Layer Security or EAP-TLS. These two EAP flavors are the most popular for wired 802.1X deployments. Both protocols utilize SSL/TLS running under EAP to authenticate the Authentication Server which sets up a secure tunnel. When shopping on the Internet, SSL/TLS is often used to protect the transaction over the network and to establish trust that the web site being contacted is really that web site and not an imposter's web site. A cornerstone of trust in SSL/TLS is the digital certificate. For PEAP and EAP-TLS, the Authentication Server sends over a digital certificate which the supplicant will attempt to validate. After a series of checks are performed, the supplicant will need to establish that the digital certificate was created by a trusted authority. If it passes that test, an SSL/TLS tunnel can be established. At this point, PEAP and EAP-TLS diverge. PEAP uses the tunnel to securely pass credentials via another protocol, typically a username and password, to the Authentication Server while EAP-TLS uses a client digital certificate for authentication. Because how digital certificates are created and validated, we will need to cover them in depth. Public Key Infrastructure and Public Key Certificate Basics Have you ever seen the warning dialog shown in Figure 8 when using https:// (e.g., going to any secure web site, such as a login or shopping cart) in a web browser? Figure 8 - Security Alert This dialog is entitled "Security Alert" and it talks about something called a "security certificate". What is a security certificate? NOTE: A security certificate, digital certificate, public key certificate, and identity certificate are different terms which all refer to the same thing in this whitepaper. Well, a security certificate is there to help identify the web site as one that can be trusted. However, the Security Alert dialog is telling us that we may not want to trust this security certificate - which indirectly means that this web site may not be the web site we think it is. There are two warning icons associated with this dialog. The help text by the first warning icon prompts us to view the certificate. Let's click on "View Certificate". 7